IML - Radare2 Reverse Engineering: Ep.2 – Windows Binary Part 2
Radare2 Reverse Engineering Ep.2 - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
IML - Radare2 Reverse Engineering: Ep.2 – Windows Binary Part 2
- We can read all the strings in the binary with:
1
2
izz
or to be more precise - we can do:
1
2
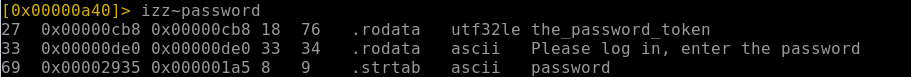
izz~password
And we get the password:
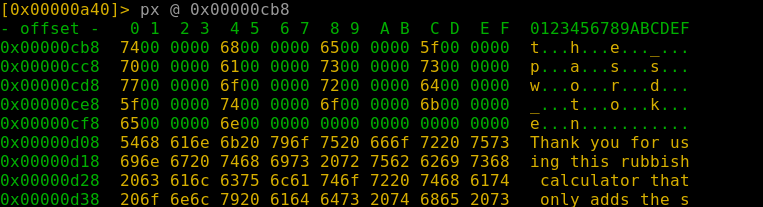
the_password_tokenNow if we take the address of the password - we can print out a block starting at that position:
And we get the address of the 7th character
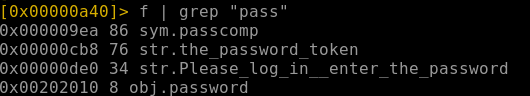
- To get the password compare function we can do:
1
2
f | grep "pass"
This post is licensed under CC BY 4.0 by the author.